CryptoCurrency Security Standard (CCSS) Updated to Version 9.0
Focused on private key management, this critical update stands to strengthen security across the crypto industry and is strongly recommended for adoption
Version 9.0 of the CryptoCurrency Security Standard (CCSS) has been published! The Standard is a vital framework designed to safeguard cryptocurrency systems, particularly in the area of private key management. With the rise of high-profile hacks targeting private keys, the necessity of a rigorous, community-driven standard is more pressing than ever.
Since its initial release in 2015, the CCSS has been developed and maintained through community collaboration, ensuring it remains free from corporate ownership or control. This neutrality ensures that updates, including the latest 9.0 release, focus entirely on enhancing the security of the cryptocurrency ecosystem.
“As part of the update project for CCSS version 9.0, the CCSS Steering Committee launched a stakeholder's feedback program encouraging the community to review the draft CCSS version and provide suggestions. The response exceeded expectations, and many suggestions were incorporated into Version 9.0. This is where community-driven standards excel by leveraging the vast skill and experience in the community.” said Marc Krisjanous, Associate Director of SixBlocks Audit and a member of the C4 Steering Committee.
The Importance of Private Key Management
Private keys are the cornerstone of cryptocurrency security. The loss or theft of a private key can lead to catastrophic and permanent financial damage. Despite advancements in blockchain technology, improper private key management—whether through weak storage practices, unauthorized access, or insecure custodial solutions—continues to result in significant breaches. These incidents have cost the cryptocurrency community billions of dollars and undermined public confidence in the safety of digital assets.
"Private key management is critical to the survival and growth of the cryptocurrency industry," said Jessica Levesque, Executive Director at C4. "The release of CCSS Version 9.0 demonstrates the importance of keeping security standards up to date. When private keys are compromised, the consequences are irreversible, making it essential that our community of experts continually refines best practices for managing these keys."
CCSS Steering Committee Chair S. Dirk Anderson added, "Because no company controls the CCSS, the focus is always on the long-term security of the entire ecosystem, rather than on protecting specific corporate interests. This ensures the standard reflects the needs of the industry as a whole."
Key Updates to CCSS Version 9.0:
- Enhancement and clarification of existing requirements wording, including consolidation of the terminology used, replacement of terms and statements that restrict the use of new technologies, and more clarity on referencing external standards, making CCSS easier to understand and implement.
- New requirements addressing emerging security challenges within decentralized finance (DeFi) and other blockchain-based technical components, such as smart contracts, which introduce more complex key management systems.
- New governance requirements include written acknowledgements from executive management and key custodians, risk management, threat modeling, and service provider management.
- Enhancement of the logging aspect by adding monitoring requirements to ensure log event records are collected and monitored for suspicious activity, and (2) wallet addresses receive the same scrutiny.
- Support for single-signer mechanisms. Though not considered best practice, single-signer mechanisms are used in many architectures. The latest CCSS update provides detailed considerations when evaluating the use of a single-signer mechanism.
- New requirements addressing physical security controls within environments where key management activities are conducted.
- New requirement for training for personnel involved in key management operations and personnel who could impact the security of the key management system.
The updated Standard can be found in our CCSS v9.0 Matrix.
An overview of updates can be found in our summary of changes document.
A Continued Focus on Community Leadership
The CCSS Steering Committee, composed of leading security experts and blockchain technology professionals from around the globe, oversees each update to ensure the Standard remains relevant in the face of new threats. Importantly, no corporations pay to participate in the creation or update of the standard, allowing the committee to maintain its focus solely on improving the security of the cryptocurrency industry.
"The collaborative nature of the CCSS is key to its ongoing success," said Jameson Lopp, Co-founder and Chief Security Officer of Casa, and a C4 Steering Committee Member. "Because the people contributing to the standard have no vested interest in promoting any particular company or product, the standard remains an objective measure of security best practices."
As the cryptocurrency industry continues to evolve, security must evolve with it. The CCSS plays a vital role in protecting the assets and trust of users, ensuring that as the industry grows, it remains safe for adoption on a global scale.
How to Get Involved
Contributing to the development of the CCSS is open to anyone and free of charge. Blockchain developers, security professionals, and cryptocurrency enthusiasts are encouraged to join the effort to secure the future of cryptocurrency.
For more information about the CCSS or to learn about certification opportunities, please visit cryptoconsortium.org.
About C4
The CryptoCurrency Certification Consortium (C4) is a nonprofit organization dedicated to establishing and maintaining security standards for the cryptocurrency industry. Through education, certification programs, and community collaboration, C4 works to ensure the responsible use and secure development of blockchain technology. Visit the website, follow C4 on LinkedIn, or “Subscribe” on YouTube.
Media Contact: Info@cryptoconsortium.org
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Announcing the New Chair of the CCSS Committee: S. Dirk Anderson
The CryptoCurrency Certification Consortium (C4) is thrilled to announce that S. Dirk Anderson, CRISC, CISA, CBP, has been appointed as the new Chair of the CryptoCurrency Security Standard (CCSS) Committee. Dirk will be taking over from Petri Basson who has led the committee since August of 2019. This milestone marks the next chapter in C4’s mission to establish and promote security best practices for cryptocurrency systems.
A Legacy of Leadership
S. Dirk Anderson is no stranger to C4 and its community. Having served as the chair of the Certified Bitcoin Professional (CBP) committee since 2019 Dirk has demonstrated his ability to foster collaboration, drive innovation, and maintain the highest standards of excellence. For the past five years, he has also been a key member of the CCSS committee, contributing his expertise and helping shape the CCSS into what it is today.
Dirk is currently the founder of the Imagine Crypto consultancy before which he was the Chief Operating Officer at SALT Lending. As a cryptocurrency, technology, and cyber risk professional with over three decades of experience, Dirk has a proven track record of addressing the unique challenges of blockchain technology. His insights have been instrumental in ensuring the CCSS, which was first published in 2014, is regularly updated and remains relevant in an ever-evolving crypto landscape.
The Importance of the CCSS
The CryptoCurrency Security Standard (CCSS) is the industry's benchmark for assessing the key management security of cryptocurrency systems. It provides clear requirements and best practices for securing keys, wallets, exchanges, and other critical components of the blockchain ecosystem. With increasing threats to digital assets, the CCSS is more relevant than ever in ensuring confidence and trust in cryptocurrency systems worldwide.
“Security is the foundation of trust in the cryptocurrency ecosystem,” Dirk said in a recent interview. “The CCSS plays a critical role in setting the bar for how digital assets should be safeguarded. As adoption grows, so too does the responsibility to ensure the tools and systems we use are secure and resilient.”
“The CCSS is more than just a set of guidelines—it’s a vital framework for building trust and security in the cryptocurrency space,” Dirk said. “I’m honored to take on this role and continue the incredible work Petri Basson and the committee have accomplished. As the industry evolves, so must the CCSS, ensuring we remain at the forefront of safeguarding digital assets.”
C4’s executive director, Jessica Levesque, shared her confidence in Dirk’s leadership, saying, “Dirk has demonstrated exceptional dedication and vision throughout his time with C4. His expertise and passion for advancing cryptocurrency security will ensure the CCSS remains a critical resource for organizations worldwide. We are thrilled to have him as the new Chair.”
A Vision for the Future
As the new chair, Dirk is committed to expanding the CCSS’s reach and impact. His vision includes greater adoption of the standard by organizations worldwide, as well as continued collaboration with industry experts to ensure the CCSS evolves alongside technological advancements.
“One of the greatest strengths of the CCSS is its ability to bring together professionals from diverse backgrounds to solve complex security challenges,” Dirk remarked. “I’m honored to lead this committee and work with such a talented group of individuals to advance the standard.”
A Note of Thanks
C4 would like to extend its deepest gratitude to the previous committee chair, Petri Basson, for his dedication and contributions. Petri’s work has laid a strong foundation upon which Dirk and the committee will continue to build and he will be staying on as a member of the steering committee.
Join Us in Congratulating Dirk
Please join us in congratulating Dirk Anderson on his new role as Chair of the CCSS Committee. Under his leadership, we are confident that the CCSS will continue to set the global standard for cryptocurrency security.
To learn more about the CCSS or get involved, visit C4's website.
Feel free to share this announcement and celebrate the next chapter for the CCSS and the incredible team driving it forward. Together, we can build a safer and more secure blockchain future.

C4 Welcomes Rodney MacInnes as New CBP Committee Chair
The CryptoCurrency Certification Consortium (C4) is pleased to announce Rodney MacInnes as the new Chair of the Certified Bitcoin Professional (CBP) Committee. Rodney brings five years of dedicated service to the CBP Committee and a wealth of professional expertise from his role as CRO and AML Compliance Ninja at Outlier Compliance Group. His leadership will usher in an exciting new chapter for the program.
Released in 2014, alongside C4’s inception, the CBP was the first certification of its kind, setting the standard for Bitcoin proficiency worldwide. Over the years, the program has been continually updated to ensure it remains current, relevant and valuable as the Bitcoin landscape evolves. With thousands of Certified Bitcoin Professionals globally, the CBP equips individuals with the knowledge and credibility needed to navigate and contribute responsibly to the Bitcoin ecosystem.
Rodney reflected on his new role: "Bitcoin’s relevance has never been greater, and the need for trusted education and proof of knowledge is critical. I’m honored to lead the CBP Committee as we continue to provide professionals and organizations with the tools to engage with Bitcoin responsibly. The CBP is a symbol of trust and competence in the crypto industry."
S. Dirk Anderson, the outgoing CBP Chair, expressed confidence in Rodney’s ability to elevate the program further: "Rodney has been an invaluable member of the CBP Committee for years. His vision and expertise are exactly what the program needs to stay ahead of the curve and continue driving meaningful impact."
C4 and the CBP Committee offer a robust prep course and prep book to help candidates succeed, and the certification itself demonstrates a foundational understanding of Bitcoin’s principles, operations, and security. Additionally, the CBP Committee regularly conducts livestreams for free educational events, making unbiased, accessible education available to the wider community. This is only possible because of the dedicated committee members who bring deep expertise, keep up with the ever-evolving technology, and ensure the content remains relevant and valuable. With members from diverse professional backgrounds, the committee ensures a well-rounded, impartial approach to Bitcoin education.
Hunter Albright, a fellow CBP Committee member, shared his excitement about Rodney’s new role: "Rodney’s experience and commitment to C4 make him the perfect choice for Chair for the CBP committee. Working on this committee has been both rewarding and enjoyable—we’re a team that takes the mission seriously but also knows how to have fun while doing meaningful work."
Jessica Levesque, Executive Director of C4, highlighted the program’s impact: "Bitcoin education is hard to find without bias, and that’s where the CBP stands out. It’s a trusted resource that brings together insights from a variety of experts. Rodney’s leadership will ensure the CBP continues to thrive as the go-to certification for Bitcoin professionals."
The CBP program remains a cornerstone of C4’s mission to advance knowledge and professionalism in cryptocurrency. With Rodney MacInnes at the helm, supported by a passionate and diverse committee, the future of the CBP is brighter than ever. Stay tuned for upcoming educational events and updates as Rodney and the CBP Committee continue to lead the way!
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Crypto Compromise – Data Breaches and Security Scenarios
Overview
Unfortunately, data breaches happen. Any company, service, or piece of software may experience compromise at some point. Engineering secure software is a difficult challenge despite the best efforts of developers, and hackers continue to evolve their tactics. But what happens when there is a data breach, and what are some ways that an attacker can use stolen data to steal valuable information or even money? In this article, we’ll discuss two examples of data breaches that affect the cryptocurrency world in particular. We will discuss what kind of data can be stolen, how the compromise can affect users, and what individuals can do to mitigate those effects on their security and privacy.
Password Manager Breaches and Crypto Theft
The first breach in our list is that of LastPass, a cloud password manager. LastPass (and other password managers) allow users to securely store, generate, and autofill passwords and other secrets for various services. The user specifies a master passphrase that only they know, which is used as a key to encrypt the password vault using strong encryption. In order to access the secrets inside, a user must specify that master passphrase to decrypt the data inside.
This allows users to store lots of long, strong, randomly generated passphrases that a user could not remember on their own. A password manager is an excellent security tool for this reason, as it prevents password reuse and allows the use of stronger passphrases. However, the security of the master passphrase is critically important. If the vault uses strong, properly implemented encryption such as AES, the only way for an attacker to gain access to the data inside is to guess the password.
In August of 2022, LastPass experienced a breach where the encrypted vaults were stolen from LastPass. LastPass and other password manager companies don’t know or store your master passphrase, just the encrypted vaults. The attackers now have snapshots of those vaults from the time of compromise. But what does that mean for users? In order to gain access to the secrets stored inside, the attackers must try to crack the password using something like a brute- force or dictionary attack. This does take a lot of computing resources, but in some cases is quite worth the reward.
Unfortunately, some users did not use the best master passphrases possible. Those compromised vaults, in some cases, contained a juicy reward for the attackers – cryptocurrency seed phrases! Some users of LastPass that stored seed phrases in their vaults have had their cryptocurrency stolen as a result, as anyone that has the seed has access to the coins. A BIP39 passphrase, preferably not stored online or not stored with the seed, could have added an additional layer of protection.
It is absolutely critical that users of any password manager generate a very long, strong, high entropy passphrase to protect their vault. The master passphrase, in this case, is the weakest link in the chain. Compromise the passphrase, compromise the vault and all the secrets inside. It’s also important if you’re the victim of such a breach to be proactive. Move your secrets to a new platform, rotate the secrets (seed phrases, passwords, etc.) to new ones, and choose a new master passphrase. Active management of your data can mitigate the effects of such a compromise.
Crypto Company Email Leaks
Another, perhaps more straightforward data breach to understand occurred with CoinMarketCap, a cryptocurrency market information platform. The emails of over 3 million users were exposed – no passwords, just emails. It might seem that this is a relatively tame breach, as the attackers cannot directly crack and takeover accounts without a password breach.
However, emails allow a common vector of attack to flourish – phishing. One of the most effective ways for an attacker to compromise a user account isn’t technical, it’s human. Phishing is the act of tricking a user into giving up information that they shouldn’t such as a password or a crypto seed phrase. If your email is included in a data breach such as CoinMarketCap’s, it tells hackers something about you – that you use or are interested in cryptocurrency.
As such, attackers have used emails in this breach to send out all sorts of crypto-related phishing emails – pretending to be CoinMarketCap, Coinbase, Gemini, Metamask, and other crypto services, coins, airdrops, and more. Victims of this breach have been targeted with these wide-ranging phishing emails in the hope that users inadvertently give up a seed phrase, a password, or sign a malicious contract. In this case, it’s critical that users have awareness about phishing. Users should know what to look for when it comes to phishing – a sense of urgency, a too good to be true offer, coming from a different email than expected, and more. Again, active awareness and self-education is a key to preventing compromise.
Awareness and Activity
Breaches happen in the digital world, and crypto-related breaches can be particularly devastating as they have financial consequences. Two examples include the breach of password managers containing seed phrases or exchange credentials, and email breaches that make users the target of sophisticated phishing attacks. In both cases, active awareness is important for user security. Taking the time to educate oneself about phishing may prevent falling victim to theft. If a user knows they’ve been compromised in a password manager breach, taking the time to rotate credentials and choose a new master passphrase on an immediate basis, can help avoid loss.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

MultiSig Wallets & Addresses: How They Work and Their Role in Crypto Security
Multi-signature (Multi-Sig) wallets use a security mechanism where multiple keys are required to authorize a cryptocurrency transaction. This added layer of protection makes Multi-Sig wallets a popular choice for both institutional and retail investors. However, the increased security comes with added complexity, so it's important to understand the risks before using them.
Multi-Sig Explained
In the world of cryptocurrency, the adage "not your keys, not your coins" still holds true. Securing your private keys is crucial, and one of the key methods is through a Multi-Sig wallet. A Multi-Sig wallet requires multiple cryptographic keys, and a threshold number of these keys must be used to authorize a transaction (tx). By eliminating the reliance on a single key, Multi-Sig wallets significantly reduce the risk of fraud, as no single person can complete a transaction alone.
Types of Multi-Sig
There are two main types of Multi-Sig implementations:
Pure Multi-Sig (Different Private Keys)
This type uses different private keys for each holder. For example, in a 2-of-3 setup, there are three private key holders, and at least two of them must sign the transaction for it to be approved. This approach is particularly suited for institutional users who require a high level of security and accountability.
Two-Factor Authentication (2FA, Same Private Key)
In this setup, a single private key is used, but it's distributed across multiple devices (e.g., laptop, phone, tablet). Each device has its own PIN or passphrase to add an extra layer of security. The user needs approval from a set number of devices (m-of-n) to finalize a transaction, offering a simpler form of Multi-Sig.
Blockchain Support for Multi-Sig Wallets
Bitcoin
The Bitcoin blockchain natively supports multi-sig addresses and security at the platform level. Its scripting language allows for seamless multi-key transactions, ensuring secure Multi-Sig operations.
Ethereum
The Ethereum blockchain, on the other hand, is account-based and limits private key usage to a single key for basic ETH transactions. However, through smart contracts, Ethereum can support Multi-Sig by allowing multiple private keys to interact within the contract.
Drawbacks & Challenges of Multi-Sig
While Multi-Sig wallets offer increased security, they come with challenges. Managing multiple private keys or devices with the same key but different PINs can become a significant burden. The risk of losing one or more keys grows as the number of keys increases, and this expanded scope of security management can complicate things. Furthermore, defining thresholds carefully is essential—using n-of-n instead of m-of-n means that all keys or devices must be available to authorize a transaction, which can introduce critical points of failure.
Conclusion
Multi-Sig wallets offer a robust security solution for institutional and retail investors alike. However, they require careful configuration and management. A thorough understanding of how Multi-Sig works, along with secure storage and usage practices, is essential to ensure the safety of your crypto assets.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Taher Borsad.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Expanding Excellence: C4 Exams Transition to New and Improved Testing Platform
A Unified, Enhanced Testing Experience
This transition not only enhances the user experience but also aligns with our commitment to maintaining the highest standards in cryptocurrency education and certification. The new and improved testing platform offers a seamless, intuitive user interface and provides valuable insights into test results, ensuring that every candidate experiences an efficient and comprehensive testing process. With these upgrades, candidates for the CBP (español), CEP and CCSSA certifications will enjoy the benefits of real-time scoring, instant feedback, and a flexible schedule for taking the exams online.
Updated Pricing Structure
In our ongoing effort to deliver exceptional value and quality, we've updated our exam and certification pricing. The revised fees will include the initial exam cost, one retake (if needed), as well as a digital certificate. Printed certificates will continue to be available for a nominal shipping fee.

Users who have already paid the exam fee with C4 may contact certifications@cryptoconsortium.org for assistance.
How to Proceed
To register for the CEP, CCSSA, or any other C4 exam, or to renew your certification, please visit our website. https://cryptoconsortium.org/get-certified/
Conclusion
C4's commitment to fostering professional growth and enhancing security practices within the cryptocurrency space continues with these exciting updates. Whether you are a new candidate aiming to certify your expertise or a returning professional seeking to renew and refresh your knowledge, our new platform and its features are here to support your journey in the cryptocurrency world.
If you have any questions or concerns, please contact us at certifications@cryptoconsortium.org.

Overview
Self-Custody cryptocurrency wallets, otherwise known as noncustodial wallets, represent the heart of decentralized blockchains - self sovereignty! With a noncustodial wallet, users hold their own keys to their money, retaining full control over their transactions, security, and privacy. Self-custody wallets allow for maximum control, but they also require a user to fully create and understand their own security posture. Let's discuss some of the pros and cons of self-custody wallets, how to choose one, and basic security tips.
Pros and Cons of Non-Custodial Wallets
There’s a classic saying in the crypto world: “Not your keys, not your coins.”The biggest pro of self custody is full control and self sovereignty. With these wallets, the users hold their own keys, giving them full access to their coins or tokens without having to rely on a third party. With this model, there's no counterparty risk - meaning there's no third party you have to trust to hold or secure your money. You are solely responsible for handling your keys securely. There's no ability for anyone else to lock you out of your funds or lock you into a particular wallet - you can transfer your keys to any software that supports standard private keys and seed phrases.
Self-Custody wallets are the most accessible to anyone, anywhere in the world. All a user needs is a phone or PC and an internet connection to download wallet software. There's no requirement for ID, a bank account, or even a permanent address to use a cryptocurrency wallet. There's also software for every need, ability, and threat model - from very easy-to-use wallets to feature rich "power user" software for the tech-savvy and perhaps paranoid!
However, there are some cons to this model of full private-key control. With noncustodial wallets, again, you are fully responsible for your money. While that provides autonomy, it also means you are solely responsible for ensuring the security of your keys. If you make mistakes in storage, or accidentally reveal your keys to an attacker, your coins will be lost. There's no support team or helpdesk to reach out to or chargeback mechanism on the blockchain. It's critical for users to understand security best-practices and implement them for their own needs.

Choosing a Self-Custody Wallet
Self-custody wallets come in several forms, most often sorted by the device you run the software on. In general, there's three major types of noncustodial wallets:
- Desktop/Web Wallets
- Mobile Wallets
- Hardware Wallets
First, desktop and web wallets. An example of a web wallet would be the MetaMask wallet. These wallets are generally the least secure of the 3 classes, due to the highest attack surface. With web wallets especially, there's a wide variety of methods attackers can use to compromise them, such as fake-but-convincing websites that pretend to be your wallet (phishing), Javascript/web application vulnerabilities, and the like. Web wallets are not advised.
Desktop wallets such as Electrum can be slightly more secure, but suffer from similar potential problems. Malware that steals key files can take a copy of your wallet, and address-swapping malware (address poisoning) attacks can replace copy-pasted addresses you use for transactions with that of an attacker. All of this is not to scare you, but advise that desktop and web wallets have a higher degree of risk than other types. They can be used safely, but require vigilance and a well-secured device.
A better option for an easy-to-use wallet would be a mobile wallet, an app installed on a smartphone. Mobile wallets are often designed to be user friendly, and offer quick access to your coins for everyday transactions. Mobile operating systems are more "locked down" than desktops. Although not invulnerable, they are less likely to suffer from problems with malware as users only install software from app stores, where applications are vetted for malicious code. Mobile wallets, like desktop and web wallets, store an encrypted copy of the keys on the device, so make sure to choose a strong wallet passphrase.
The third and most secure type of self-custody wallet is a hardware wallet. These include wallets like Trezor, Ledger, or KeepKey. These are specialized devices designed to do one thing - generate and store cryptocurrency keys securely and use those keys to sign transactions. They don't run any other software or even connect to the internet. This type of wallet has the smallest attack surface, and therefore fewer chances for an attacker to compromise your keys. These do cost more money than desktop or mobile wallets, which are usually free. A hardware wallet will often cost around $50 USD, which may be expensive for users new to cryptocurrency.
Seed Phrase Basics
Almost all modern wallets, whether desktop, mobile, or hardware, will give the user a seed phrase. This phrase of 12-24 random English (or local language) words encodes all of the user's private keys in a simple format. The seed is used to access all of the cryptocurrency in that wallet, so it is critical to safeguard this phrase.
For a desktop or mobile wallet, it is okay to store an encrypted form of that seed in software such as a password manager, protected by a long strong passphrase. However, there are some risks associated with doing so. It's preferred to write down a seed phrase on paper or metal, and store that in a safe location.
For a hardware wallet, you must only write that seed on paper or metal, and never type it into any general-purpose computer like a phone or PC even if it's encrypted. The security model of a hardware wallet is to generate and store keys offline - so doing this basically turns a hardware wallet into a normal desktop or mobile wallet. Your security is no longer that of an offline hardware wallet, it's only as good as that phone or PC you're storing a copy of the seed on! It doesn't mean your money will be instantly stolen, but you'll have less security than you think you do.
No matter what type of wallet, never store a copy of the seed in plain-text form on a computer. Do not type your seed into a Google Doc, a .txt file, or even take a picture of it with your phone. Malware and other sophisticated attacks can search your PC for this information if it is compromised, and use the seed to steal all of your coins. Also, make sure that no matter how you store your seed you make backups. If on paper, place a copy in another safe location so that fire or flood does not completely destroy the keys. If stored in encrypted form, make sure there's backups of that vault. Losing your seed means losing your coins, so it's critical you always have access to that information.
Self Custody Sovereignty
Self-custody wallets give users the best of cryptocurrency - full control! You can use your coins any time, anywhere in the world without relying on third parties. No ID, no KYC, no lockouts or inconveniences of traditional banking. But with this power does come additional responsibilities. You are fully responsible for the security of your coins. Make sure to choose a secure, well vetted wallet that fits your needs. For small amounts of spending money, a mobile wallet is the best choice. For larger amounts or long-term storage, a hardware wallet will offer additional security. In either case, secure storage of the seed phrase is important. Make sure your seed phrase is stored somewhere safe on paper or metal, and make and store safe backups. Make sure you don't lose that seed phrase; keep yourself safe and sovereign with your coins!
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Overview
In the rapidly evolving world of cryptocurrency, the sanctity of one's crypto assets is paramount. As digital thieves become more sophisticated, so must our defense mechanisms. One of the primary tools at our disposal to fortify our accounts against unauthorized access is Multi-Factor Authentication (MFA). This blog explores what MFA is, the types of authentication factors involved, and crucial steps to ensure you utilize MFA optimally for your crypto exchange account.
What is Multifactor Authentication?
At its core, MFA is a security process that requires an additional step for verification instead of relying solely on a password. MFA adds additional layers of security, thereby drastically reducing the chances of unauthorized access.
Imagine a high-security facility. Instead of just one lock on a door, the user might have to have a key and swipe a badge to open the door. Similarly, with MFA, even if a cyber-thief manages to get past one layer (e.g., knows your password), they still have more hurdles to clear before accessing your account.

Types of Authentication Factors
Authentication factors for MFA can generally be categorized into:
- Something you know: This is the traditional password or PIN. It's something that you've memorized and can recall upon request.
- Something you have: This refers to a physical device in your possession, such as a security token, a smart card, or even your smartphone where you might receive a one-time code via SMS or through an authenticator app.
- Something you are: These are biometric methods of identification such as fingerprint scans, retina scans, or facial recognition.
For crypto exchanges, a common combination involves using a password (something you know) and then a code generated by an authenticator app or received via SMS (something you have).
Turn MFA On ASAP!
Given the value and volatility of crypto assets, it is crucial to turn on MFA for your crypto exchange account immediately if you haven’t already. While it might seem like an extra step during login, the benefits in terms of account security are immense. Without MFA, if someone manages to get a hold of your password, they have instant access to your funds. With MFA, that password alone is useless to them.
Backup Your MFA Codes
Most platforms, when setting up MFA, will provide you with backup codes. These are crucial. If for some reason, you lose access to your primary MFA device (e.g., you lose your phone), these backup codes will be your ticket back into your account.
- Store them securely: These codes are as important as your password. Print them out and store them in a safe place, away from prying eyes.
- Avoid digital copies: It's tempting to screenshot or save these codes in your email. However, if your email gets compromised, these backup codes can be a goldmine for hackers.
- You can instead store these securely in a password manager. Keep in mind though that doing so means your accounts may still be compromised in the event your password manager is hacked. You may wish to store your 2FA codes separately or ensure your password manager is also protected by 2FA.
Securing Your MFA Codes
- Securely Store Backup Codes: Treat MFA backup codes with the same level of care as you would a password. Keep them in a safe and separate location, away from your primary device. Consider using a physical safe or a secure digital storage option like a password manager.
What Not to Do:
- Avoid Storing Backup Codes on Your Primary Device: It's essential to refrain from saving backup codes on the same device you use for MFA. Losing your device means losing access to your backup codes as well.
- Limit Access to Backup Codes: Share backup codes sparingly, if at all. They should be reserved for emergencies, preferably for your use only. Avoid placing them in easily accessible locations like your wallet or on sticky notes.
Good habits:
- Regularly Review and Replace Backup Codes: Be proactive and periodically review your backup codes. Make sure you have a sufficient supply of unused codes. If you're running low, generate a fresh set.
- Enable Account Recovery Options: Take advantage of account recovery options provided by some services. These options often involve setting up a secondary email address or phone number. Ensure that these recovery options are up-to-date.
- Test Backup Codes: Before you actually need them, verify the functionality of your backup codes. This way, you can be confident they will work when required.
- Understand Expiry Dates: Keep an eye out for any expiry dates on backup codes set by platforms for security reasons. Replace any expired codes as necessary.
- Generate New Codes if Compromised: If you suspect that your backup codes have been compromised, generate a new set immediately. Treat this process like changing a potentially exposed password.
- Regularly Review MFA Settings: Periodically check your MFA settings on each platform to ensure correct configuration. Make any necessary updates or changes.
- Consider Using Hardware Tokens: Instead of relying solely on backup codes, consider the use of physical hardware tokens for MFA. These convenient devices generate one-time codes and enhance security.
Summary
In a realm as dynamic and promising as cryptocurrency, security is paramount. Multi-Factor Authentication offers an invaluable layer of protection for your crypto exchange account, shielding your investments from potential unauthorized access. Major exchanges such as Coinbase support strong 2FA like auth app and security keys, so take advantage of that for better security. By understanding its importance, enabling it promptly, and ensuring that backup codes are securely stored, you make a significant stride towards safe and worry-free crypto trading. Don't wait – secure your crypto future with MFA today!
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Manan Vora.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Introduction
The CryptoCurrency Security Standard requires a Data Sanitization Policy as part of the 2.02 Data Sanitization Policy Aspect of CCSS. This aspect involves the elimination of cryptographic keys, seed phrases, and any sensitive information related to key management. Thorough sanitization guarantees the complete destruction of all sensitive information, thereby preventing any potential for data breaches from devices that are no longer in use. These devices include steel plates used for recording seed phrases.
One of the methods for recording seed phrases or passphrases long-term is to punch the 12-24 words from a mnemonic phrase onto steel plates. Steel plates are a popular method because they are not susceptible to electromagnetic attacks, fire (temperature-dependent on metal type), flooding, and are also resistant to other disaster scenarios. Steel plates are more resilient than storing secrets on paper, and less risky, in terms of data degradation and accidental data loss, than storing them on digital media.
However, this begs the questions: How might one go about sanitizing secrets that have been stored on a steel plate? Sanitizing data in accordance with CCSS requirement 2.02.2.1 requires that sanitized media conforms to the National Institute for Standards and Technology (NIST) Special Publications 800-88 recommendation to “clear, purge, or destroy” the media.
As a CCSSA, I have previously completed a CCSS audit and I am part of C4’s CCSS Advocacy Group. As a security advocate, I set out to determine what constitutes ‘cleared’ data for steel plates. Clearing the data is the most realistic method of data sanitization of a metal plate as most will not have access to a furnace that can reach the temperature required to melt metal.
The following walks you, the reader, through this process.
The question I am seeking to answer is:
After you punch your seed phrase or secret onto a steel plate, how effective is it to overwrite that data using this ‘Clear’ method of sanitization? Can the secret be recovered after performing the ‘Clear’ method of overwriting data?
Follow along to see!
The Set-Up
To test the ‘clearing’ of a steel plate, first I purchased a set of steel plates and punches.

To start the experiment I punched the secret ‘PASS123’ into the first cell on the steel plate. This is being used in lieu of a secret seed phrase and will be the data punch and then destroy in each of these attempt. For each type of data destruction I will punch the seed phrase in the same manner and then attempt to destroy the data using different methods.

The Experiment
In this section, I will use a myriad of different “common” hand tools to test their effectiveness and efficiency for sufficiently wiping data punched into steel plates. The purpose of this continued experimentation is to try and find a more time efficient way to destroy the secret punched into the steel plate. I’m going to use the same secret as the above example for each of the tools demonstrated below.
Letter Punch
To keep this simple, I will overwrite the secret with a series of letters and numbers and then check if "three passes," as mentioned in the NIST 800-88 specification, will be sufficient to make the secret unreadable and unrecoverable.
On my first pass to overwrite the data I used the same lettered punches that I used to embed the secret, using an 'X' punch. You can still clearly see the secret.
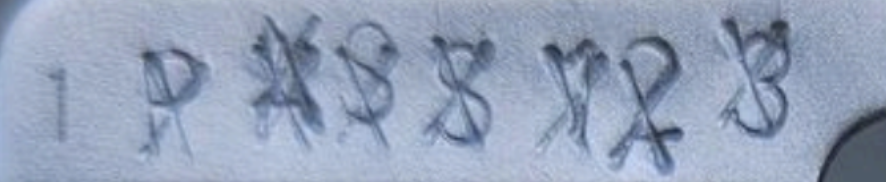
On my second pass to overwrite the data, a 'W' punch was used.
Some of the secret is still visible: The ‘P', the ‘S’s, and ‘2’ and '3’.

On the third pass, I used a number '8' punch.
We can see after the third pass most of the secret is no longer readable, although I can still kind of make out the '2'. If this was a real secret, another pass with another punch would be a good idea to further destroy the original secret and make it unrecoverable.

Using additional punches to overwrite the secret data punched into steel plates until it is no longer readable/recoverable, does seem to be possible to effectively make a secret punched into steel plates unrecoverable using the ‘Clear’ method of data sanitization from the NIST 800-88 standard.
For this method, I would recommend performing at least 3 passes of overwriting the secret data to make it unrecoverable. Perform more passes if the secret is still visible / recoverable.
I would also recommend using punches that cover the top and bottom of the data being overwritten, as to not reveal any information about the individual characters in the secret.
Also, be aggressive with the punches while overwriting data. Give a good punch, not a tap, to better overwrite the data. This applies to any punch method.
There are no additional tools required for overwriting the data in this manner. A potential downside to this approach is that it takes at least 3x longer to sanitize the secret than it took to initially record the secret as the data had to be overwritten 3 times, and to be most effective further overwriting would be advised. It is pretty tedious to overwrite the data character by character as the above example demonstrated.
Summary
Effectiveness: 10 (Highest)
Cost: 3
Effort: 8
Chisel
For this experiment, I used a chisel, which is a wedge shaped metal punch tool, to overwrite the secret. I did not count the number of passes, rather made enough punches for the secret to be overwritten.

This tool is pretty effective at destroying the secret data. I can still make out some of the letters such as ‘A' the ‘2’ and '3’. My chisel was used and the tip was more dull, so a sharp tip (or a new chisel) would likely perform better. The time it took was very short, about a 1 minute or <10 strikes to get the result shown below.

The cost of a set of chisels on Amazon is around $20 and would likely last for as many steel plates as you can destroy. The plate is softer metal so I can't imagine the chisels getting dulled at all from this task.
Summary
Effectiveness: 5
Cost: 3
Effort: 2
Round Tip Punch
I used a round tip punch. Again, I did not count passes, but rather made enough punches for the secret to be overwritten.

Using a round tip punch to overwrite the secret required more work than the chisel but not as much as overwriting it letter by letter. Some of these letters are still visible such as the ‘A' and the 'S’s.
I thought this tool would smush the letters and they would be so mangled they’d be unreadable. I think the effectiveness will depend on how prominent the original secret was punched into the steel.

Summary
Effectiveness: 4
Cost: 4
Effort: 5
Electric Powered Grinder
An electric powered grinder was the ultimate tool to wipe data punched in a steel plate.

The time and effort are the lowest with this tool. As shown in the photo below, I intentionally left some of the letters, but the area that was ground away leaves nothing to recover. Doing this took about 3 seconds, so the time to effectively destroy the secret is minimal.

Summary
Effectiveness: 10
Cost: 5
Effort: 1
Conclusion
In conclusion, the CCSS 2.02 Data Sanitization Policy highlights the critical need for effective methods of data destruction, including when it comes to durable and resilient mediums like steel plates. The exploratory work of CCSSA William Keppler, as detailed in this article, underscores the practical challenges and potential solutions in achieving complete data sanitization.
By experimenting with various tools and methods, from manual punches to electric grinders, Keppler has demonstrated that while traditional overwriting methods can be effective to a certain degree, more aggressive techniques such as grinding offer a far more reliable solution for ensuring that sensitive information is irrecoverable. This aligns closely with the recommendations of NIST SP 800-88, which advocates for a comprehensive approach to clearing, purging, or destroying data. For entities dealing with highly sensitive information, adhering to these stringent standards is a critical component of operational security.
This article was written by Will Keppler, Halborn.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Overview
Passwords. Everyone in the digital world has to use them, generate them, store them, remember them, and ensure they are secure. However, picking good passwords is hard, and there are many common pitfalls in the secure use of passwords. Some platforms are moving towards a passwordless future, where applications use other means of authentication - MFA apps, hardware security keys, and other methods. For the most part though, services still use passwords, and it's critical that users manage them securely. Preventing account compromise, in most cases, starts with password management.
Password Management Tips
Password Picking
Setting up a solid password involves multiple factors, but the core technical factor needed is entropy, or randomness. In simple terms, the more random a password is, the better.
Randomness makes it difficult for an attacker to guess your password. Hackers might try to guess your password right on a website, entering it into the password field directly. More likely though, they have a password hash from a data breach - a scrambled version of the password run through a cryptographically secure one-way function. They must try to guess your password until they get a matching hash, and can then use that password to log into your accounts.
But how random is random? You might think that something "goofy" is random enough. The password "sillypotato", for example. But in terms of real entropy, 2 silly words isn't really that random. An attacker with a powerful computer could guess this simple 11 character, 2 word password in seconds to minutes. It turns out humans are really bad at random generation on our own.
A better way to create secure passwords is to use tools like a password manager to generate truly random passwords, consisting of random characters selected by the computer's cryptographically-secure RNG. A truly random 20-character password might look like this - "u8XqHp6jVp7eFutm9nzz". If you have to type or easily remember a password, you can use a type of random generation called diceware, which turns the underlying entropy into a series of English (or some other language's) words. For example - "PokeParkLikeQuickHappy". This diceware phrase is generated from 13 bits of entropy per word, and ends up with 22 characters. Lastly, if you must generate the password yourself, choose a long phrase over one or two words. Generating a long sentence with meaning to you is better, for example - "HarryPotterAndTheLongStrongAccountPassphrase" is better than "HarryPotter".
You'll notice that these random passwords aren't only random, it's also longer than our example "sillypotato" password. Length is another important component of strong passwords, and ties in with the concept of entropy. The longer a password is, the more possible combinations exist. With every character added to a password, the amount of possible passwords an attacker has to guess increases exponentially. Practically speaking, an attacker with an off-the-shelf laptop can guess all possible 8 character passwords in minutes. It doesn't matter how random an 8 character password you use, because an attacker can guess all of the possible combinations quickly.
Password Management
There's another layer to password security, not just the strength of one individual password. Password reuse is a danger that must be avoided. We discussed the possibility of an attacker guessing a password via password cracking methods. And if you reuse that password across multiple services (Coinbase, Google, Facebook, Banking, etc.), the attacker has now compromised all of those services. It's critical to generate unique, strong passphrases for all the different accounts you use. So if one is compromised, the others can remain safe.
Generating strong, random passphrases may be important for security against attacks, but also come with a practical cost. How does one remember all these difficult to guess passwords? It is completely impractical, if not impossible, for a person to remember hundreds of passwords for different accounts.
In comes a piece of secure software called a password manager. Password managers are bits of software designed specifically to generate, store, and even autofill secrets - your passwords! The software encrypts all of your passwords, 2FA notes, or payment cards in a secure vault using the master passphrase as the encryption key. Users only have to remember one very long, strong, random master passphrase to decrypt the secrets stored in the manager. To access your other accounts, the manager can autofill websites' login fields or allow you to copy-paste your passwords.
Password managers are particularly useful because they prevent password reuse, and allow you to generate and store much stronger passphrases than you can remember on your own. It's critical that you choose a well-vetted, reputable password manager and generate a long, strong master passphrase for encryption.
Password Power
There's a lot that goes into day-to-day password security. The two most critical components for the average user are the strength of their passwords - in other words, their resistance to password cracking attacks. Strength comes through overall entropy - the amount of randomness and length of the password. Choose long passwords, 20+ characters or more, and randomly generate those passwords if you can. If a password must be memorable, diceware is a useful tool. If it must be self generated, make your passphrase a long sentence of words rather than one or two words.
Secondly, password management must consider password reuse and avoid it as much as possible. A secure password manager can help you by generating, storing, and autofilling each unique password for various services. It's important to choose a long, strong, random master passphrase to encrypt your password manager vault.
Password hygiene is a challenge, but understanding these basic tips will help clean up your password game and build your security skills!
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Navigating the Risks of Address Poisoning: A Growing Scam in the Crypto World
In the ever-evolving landscape of cryptocurrency, where innovation and technology leapfrog at a rapid pace, so do the strategies of scammers. One such emerging and insidious tactic is the 'Address Poisoning Scam.' This blog aims to shed light on what address poisoning is, how it works, and, most importantly, how you can protect yourself from falling victim to this cunning scam.
What is Address Poisoning?
In May 2024, the DEA lost $55,000 in an Address Poisoning scam. Address poisoning is a relatively new type of scam in the crypto world. It exploits a key feature of cryptocurrencies - the public visibility of transactions on the blockchain. Scammers target the public transaction history of users, inserting their own wallet addresses that closely resemble those of legitimate users. This subtle manipulation can easily go unnoticed but can lead to significant losses for unsuspecting victims.
How Does Address Poisoning Work?
The scam operates on the premise of human error. Most crypto users rely on copy-pasting wallet addresses when making transactions. Address poisoning takes advantage of this by 'poisoning' the transaction history with similar-looking addresses. When a user copy-pastes an address for a new transaction, they might accidentally choose the scammer's address instead of their own. Once the crypto is sent to this address, it's nearly impossible to recover.
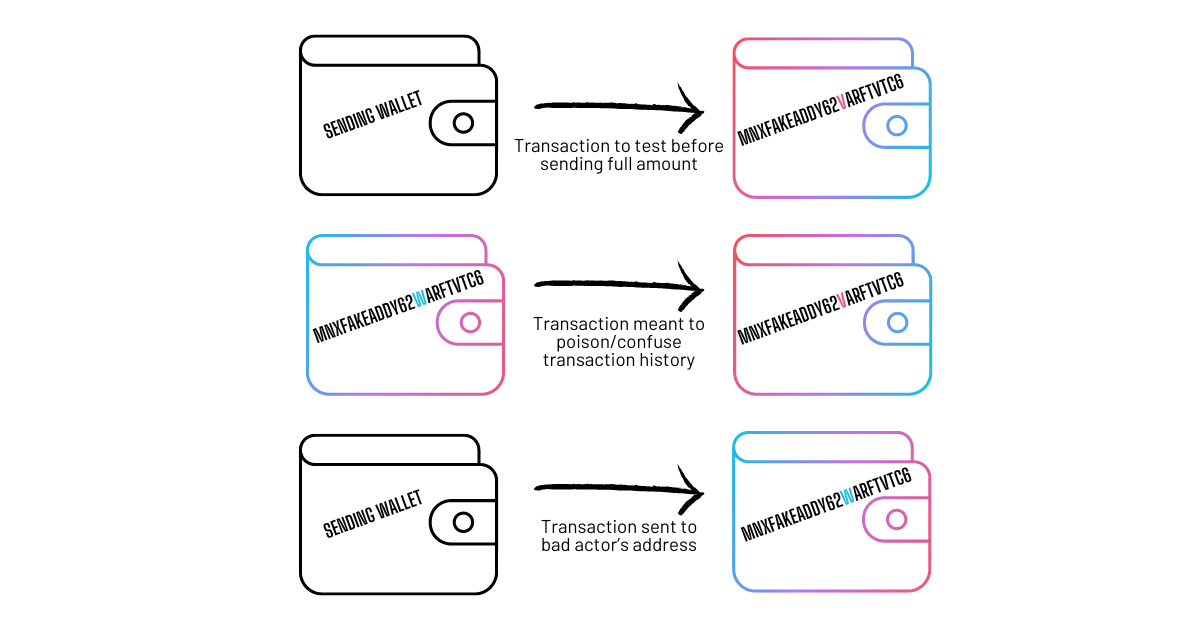
The Role of Vanity Addresses:
Vanity addresses, which contain recognizable words or patterns, can make the scam more effective. These specially crafted addresses are more memorable and can easily be confused with a user’s actual address, making the scam harder to spot.
How to Protect Yourself:
- Double-check Addresses: Always verify every character of the wallet address before confirming a transaction. This simple step can be your first line of defense.
- Use Address Book Features: Many wallets offer the option to save and label frequently used addresses. Utilize this feature to minimize the risk of selecting a poisoned address.
- Be Cautious with Transaction Histories: Be aware that transaction histories can contain these poisoned addresses. Relying solely on them for address information is risky.
- Educate Yourself: Stay informed about the latest scams in the crypto space. Awareness is a powerful tool in combating these threats.
- Use Hardware Wallets: For added security, consider using a hardware wallet, which reduces the risk of falling for such digital traps.
Address poisoning is a stark reminder that in the digital age, even the most minor details require our attention. In the world of cryptocurrency, where transactions are irreversible, the importance of vigilance cannot be overstated. By educating ourselves and adopting cautious practices, we can stay one step ahead of scammers and protect our digital assets.
Stay Safe and Informed:
Remember, the crypto journey is as much about staying secure as it is about exploring new financial frontiers. Stay safe, stay informed, and let's continue to navigate the dynamic world of cryptocurrency with confidence and caution.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Manan Vora.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Your Secret Stash: Seed Phrases, Password Managers, and Secret Hygiene
Overview
Storing a backup of your cryptocurrency seed phrase is a crucial security practice. Every user needs a seed backup in the event the original wallet software, device, or keystore is lost. However, there are often questions as to where to store that seed phrase safely. Users may be curious about store seed phrases on paper, metal, or in an encrypted form such as a secure password manager. Depending on the type of wallet, where you put your backup may reduce or compromise your security. As such, it's important to understand the relationship between the type of wallet (hot or cold) you are using and appropriate backup procedures.
First, A Note on Password Managers
A password manager is specialized software designed for storing, generating, and even auto-filling passwords. This software is designed with the secure storage of secrets such as passwords in mind. A password manager's user must only remember one very long, strong passphrase known as a master passphrase. This phrase is used to encrypt all of the passwords and other secrets stored in the password manager vault.
A password manager is an excellent security tool, as it allows users to store much stronger passphrases than they can remember for all their different accounts. Passphrases can be randomly generated strings or even random diceware passwords consisting of words. These phrases are longer and stronger than typical passwords and thus, less susceptible to attack. If a user's password hash is leaked from a company's database, it's less likely an attacker will crack that strong passphrase and take over the account.
A password manager also helps prevent password reuse. Since the user only has to remember their master passphrase, the password manager can store a unique passphrase for each account. If one account's password is somehow compromised, this prevents an attacker from using the password to gain access to another account. For example, using a unique passphrase prevents a breach at your electric provider from being used to attack your Coinbase account.
Password managers can be used to store more than just passwords. Many allow you to secure credit card information, cryptographic keys, notes, 2 factor backup codes, or other key data such as seed phrases.
Seed Phrases and Password Managers
Since password managers are purpose-built for storing secrets, is it wise to store seed phrase backups in them? It's certainly a bad practice to store seed phrases in plaintext - such as a screenshot or Google/Word document. But password managers do encrypt the secrets stored within, so what about seed phrases? The answer, like many issues of security, is it depends.
Generally speaking, storing the seed phrase for a hot wallet in a password manager is reasonably secure. To understand why it's likely okay for most use cases, we should think about the concept of hot wallets and possible attack surface for those wallets. A hot wallet is a crypto wallet that generates and stores the keys on a general purpose computer - such as a laptop or phone. These wallets include apps like Coinomi or Exodus, Electrum desktop, or the Metamask browser extension.
The key here is that storing an encrypted seed phrase in a password manager offers roughly the same security level/attack surface as the wallet itself. The wallet already generates the keys on a general-purpose computer, and stores the keys encrypted on that device (protected by a PIN, password, or other mechanism). If you store a copy of the seed in an encrypted password manager, you're also encrypting the keys on a general-purpose computer. In either case, a theoretical attack includes malware or some other exploit allowing an attacker to access the encrypted keys. If they can guess the password to the encrypted vault using password cracking techniques, they can ultimately steal the coins.
The security of your funds with a hot wallet really lies in the quality of the master passphrase for the wallet or password manager in most cases, so it's critical to choose a very strong, random master passphrase for your vaults.
But what about cold wallet seed phrases? Should you store the seed for your Trezor, Ledger, or other hardware device in a password manager? The answer is no, you should never store the seed for an offline wallet in a password manager.
Why is this recommendation different from that of a hot wallet? Again, the answer lies in the security level and attack surface the wallet is designed to have. The whole purpose of a hardware wallet/cold storage is that the keys are generated and stored offline, on a single-purpose computing device. A hardware wallet is designed to keep your crypto keys away from malware and networks, where there are more opportunities for an attacker to steal them. A hardware wallet only stores crypto keys and signs transactions offline, and does nothing else. By putting your hardware wallet seed into a password manager, you reduce the level of security to that of a hot wallet. You're now only as secure as that PC or phone, and the passphrase protecting your manager vault. You don't have cold storage anymore, you've effectively turned your wallet into a hot wallet.
Password Manager Breaches and Crypto Theft
Recent news surrounding the 2022 LastPass data breach has brought forth questions about the security of storing seed phrases in password managers. Some users of LastPass affected by this breach have reported the theft of cryptocurrency where no other avenue of compromise seems likely. So how does an attacker steal crypto from a user in this case?
In this breach, the attackers gained access to the encrypted password vaults. The data stored inside (passwords, seed phrases, etc.) can only be unlocked with the proper key. The master passphrase for the vault is used to derive the encryption key. In order to gain access to the keys, the attacker has to use password cracking techniques to essentially guess the right password. With a copy of the encrypted password vault available, the thieves could use specialized software to guess many possible password combinations using common wordlists or other techniques.
The critical line of defense in this case is the strength of the master passphrase. A master passphrase for a password manager should always be as long and as random as possible. The use of a long, difficult to guess sentence can make it infeasible for password cracking software to find a correct match. Users with weak master passwords had those passwords guessed, and once they were found the attackers could decrypt the vault and simply use the seed phrases to take the crypto in that wallet.
Seeds and Storage
When thinking about backing up seed phrases using a password manager, one must evaluate the overall security profile of their wallet. If it's a hot wallet, it is likely okay to store a copy of the seed in a password manager for safekeeping since the security level is roughly the same. For a cold wallet, it is never appropriate to store the seed in a password manager. And regardless of whether or not you choose to store seeds in a password manager, you should choose a very long, random, strong master passphrase to protect the secrets in that vault.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

What Is a CryptoCurrency Security Standard Auditor (CCSSA)?
Where there are financial services, there's risk — and with the intricacies of digital assets, we need to work diligently to assess the security of these cryptocurrency systems. That's where CCSSAs come in, turning the tide against threats with their arsenal of security savvy and CCSS know-how.
The CryptoCurrency Security Standard, developed by the CryptoCurrency Certification Consortium (C4), outlines comprehensive security requirements for systems utilizing cryptocurrencies, including but not limited to exchanges, custodians and wallets.A CryptoCurrency Security Standard Auditor, also known as a CCSSA, is an individual proficient in evaluating and assessing compliance with the CryptoCurrency Security Standard (CCSS). CCSSAs are able to apply the CCSS standard to any information system that uses cryptocurrencies, calculating a grade for the system according to the CCSS.
CCSSAs have proven their professional working knowledge in all 31 aspect controls of the CryptoCurrency Security Standard (CCSS).
Key responsibilities of a CCSSA include:
- Assessment: Conducting thorough evaluations of information systems to ensure they meet the CCSS requirements.
- Compliance Verification: Verifying that crypto asset management systems, processes, and personnel align with CCSS guidelines.
- Risk Mitigation: Identifying and addressing potential security risks and vulnerabilities with a cryptocurrency infrastructure’s key management systems.
- Reporting: Providing detailed reports and recommendations for enhancing security posture based on CCSS assessments.
CCSSAs often have to assess information systems which may have novel or unique processes, and auditors have to consider compliance to the Standard in a holistic manner which takes into account the implementation details of the information system and its ability to achieve its intended outcomes.
Once hired by an entity, CCSSAs assess if the CCSS requirements have been met - meaning the scope is defined correctly, the required security controls are correctly implemented, working as intended, and meeting the CCSS requirements for that control.
All CCSS audits cover the 12 months prior to audit completion and will test the operating effectiveness of the control over this period of time. Audits are designed to be performed at least annually. All audits performed by CCSSAs are reviewed by a CCSSA-Peer Reviewer before C4 certifies an entity.
The entire CCSS audit process is carefully designed to increase the confidence of those utilizing cryptocurrency systems, and CCSSAs are bridging the gaps between this cutting-edge blockchain technology and ironclad security.
You can learn how to become a CCSSA here. If you’re interested in having your cryptocurrency system assessed and or audited, you can find a list of current CCSSAs here: Auditor's Table
If you’re not quite ready to make the leap toward an audit, you can take C4’s CCSS Level 1 requirements training course to learn more about what the audit process entails here: Master CCSS Level 1
If you’d like to see what systems have been audited, you can view completed audits here: Completed CCSS Audits
Or head over to cryptoconsortium.org to learn all about C4’s CryptoCurrency Security Standard!
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

How is the Price of Bitcoin Determined?
The Economic Dynamics of Bitcoin’s Supply and Demand
The price of Bitcoin, like that of other cryptocurrencies, is determined by supply and demand in the market.
This means that its value fluctuates based on how many people want to buy Bitcoin versus how many are willing to sell it. Central to this is Bitcoin's supply cap of 21 million bitcoin. This finite supply plays a pivotal role in its long-term value proposition, as the dwindling new supply amid increasing demand can lead to price appreciation over time.
Using, holding, and being paid in Bitcoin are all activities that directly contribute to its demand and, consequently, its price fluctuations.
When individuals choose to use Bitcoin for transactions, it increases its utility and demand, as more people are recognizing its value as a medium of exchange. Basically it’s about embracing a financial system that's reshaping how we view value itself.
The essence of Bitcoin lies in its use. With each transaction, we're not just transferring value; we're pursuing a future where money moves freely and securely. Holding Bitcoin—often referred to as "HODLing" in the crypto community — isn't merely an investment strategy; it's a statement of confidence in Bitcoin’s revolutionary properties. When you're paid in Bitcoin, exchange fiat for bitcoin, or store bitcoin, you're part of a growing community that sees it as more than currency; it's a new standard for financial independence.
The underlying technology of Bitcoin, blockchain technology, is a decentralized ledger that records all transactions across a network of computers. This technology matters because it offers a level of security and transparency that traditional financial systems just can’t match.
Bitcoin is a world apart from conventional fiat currencies, untouched by government decree. Here, we're all participants in shaping the future of finance.
Bitcoin's journey toward becoming a universally accepted currency is far from complete. It faces challenges in scaling to meet global market demands, enhancing user interface designs for easier access, and developing privacy tools to protect users' financial privacy. Overcoming these hurdles is not just about technological advancements but also about fostering a culture of education. Sharing knowledge and educating both our peers and the next generation are crucial steps in ensuring the success of Bitcoin.
This is why our mission at C4 is not to speculate about price, but to educate about this revolutionary technology. We’re working to demystify Bitcoin, to peel back the layers of jargon and reveal the profound impact that finance with no borders promises.
For those interested in diving deeper into the world of Bitcoin and its underlying technology, the CryptoCurrency Certification Consortium (C4) offers resources, certifications, and security standards, to help individuals gain a comprehensive understanding of cryptocurrencies, blockchain technology, and their implications for the future of finance and beyond.
Join us and learn more with C4.
You can take our course about Bitcoin right now: https://cryptoconsortium.thinkific.com/courses/CBP-course
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Introduction
Non-fungible tokens, or NFTs, have taken the world by storm. These unique digital assets are revolutionizing the way we think about ownership, value, and authenticity in the digital realm. From digital art to virtual real estate and gaming, NFTs offer a new way to own, trade, and monetize unique digital items. But for those new to the world of NFTs, understanding the basics can be daunting. In this article, we'll provide a comprehensive beginner's guide to NFTs, including what they are, how they work, and their potential applications and impact on the digital economy.
What are NFTs?
Non-fungible tokens, or NFTs, are unique digital assets that exist on a blockchain. They are used to verify ownership and authenticity of digital items such as artwork, videos, and tweets, among others.
Each NFT has a unique digital signature, which verifies its authenticity and ownership. This signature is recorded on the blockchain, making it immutable and tamper-proof. NFTs are created using smart contracts, which are self-executing programs that automatically enforce the terms of the agreement. Smart contracts are embedded in the NFT and can be programmed to include various conditions, such as royalties for the creator every time the NFT is resold.
NFTs are mostly associated with the Ethereum blockchain, as the ERC-721 standard was specifically designed for the creation and exchange of NFTs. This standard provides a common set of rules for developers to create unique digital assets that cannot be replicated or divided. However, they are also on other chains such as Polygon and even on Bitcoin through Counterparty and RSK which use smart contracts to emulate the functionality of ERC-721 standard on Bitcoin.
Some well known NFTs are Rare Pepes, a series of digital trading cards that were created as a tongue-in-cheek reference to the popular "Pepe the Frog" internet meme. The project was launched in 2016 by a group of Bitcoin enthusiasts who wanted to experiment with creating and trading unique digital assets on the Bitcoin blockchain.
How do NFTs work?
NFTs are minted on a blockchain, a decentralized ledger that ensures secure and transparent transactions. Each NFT possesses a unique digital signature verifying its authenticity and ownership. Once recorded on the blockchain, this signature becomes immutable, ensuring it's tamper-proof.".
NFTs can be bought, sold, and traded on various platforms, including online marketplaces such as OpenSea, Rarible, and SuperRare. These platforms allow users to create and sell their own NFTs, as well as browse and purchase NFTs from other creators.
One of the main use cases for NFTs is digital art. NFTs have opened up a whole new market for digital art, with some NFTs selling for millions of dollars. For example, "The First 5000 Days" by Beeple, a digital artwork as an NFT, sold for $69 million at a Christie's auction. Other examples of NFTs include virtual real estate in blockchain-based worlds, such as Decentraland, and virtual trading cards featuring sports stars.
NFTs also provide a new way for artists and creators to monetize their work and gain exposure. They offer a way for collectors to own and trade unique digital items that cannot be replicated.
What can you do with NFTs?
With NFTs, you can buy, sell, and trade unique digital items in a decentralized and secure way. You can also display your NFT collection on various platforms, including social media and digital galleries.
NFTs offer a new way to own and trade unique digital items, and they have the potential to create new revenue streams for artists and creators. For example, the digital art marketplace SuperRare allows artists to showcase and sell their NFTs as art to collectors. NFTs can also be used to represent in-game items, characters, and experiences in the gaming industry. The blockchain-based game Axie Infinity, for example, allows players to buy, sell, and trade NFTs representing creatures called Axies. From art to gaming, NFTs have demonstrated their potential, with some selling for as much as $300,000 and others even fetching into the millions.
How do NFT royalties work?
NFTs have the potential to generate royalties for their creators or original owners every time they are resold. This is made possible through smart contracts, which are embedded in the NFT and automatically execute the terms of the agreement.
For example, a smart contract can be set up to ensure that the original creator receives a percentage of the sale every time the NFT is resold. This allows creators to benefit from the value of their work, even after they have sold it. It also provides an incentive for collectors to hold onto their NFTs, as they can potentially increase in value over time.
How do you mint an NFT?
To mint an NFT, you need to create a unique digital item and upload it to a blockchain platform that supports NFTs. This process involves verifying the authenticity of the digital item and creating a smart contract that outlines the terms of the ownership and resale of the NFT.
There are several platforms that support NFTs, including Ethereum-based platforms such as OpenSea, Rarible, and SuperRare. Some platforms allow users to create and sell NFTs in just a few clicks, while others offer more advanced customization options.
What makes NFTs valuable?
The value of NFTs is largely based on their uniqueness and demand in the market. Some NFTs have sold for millions of dollars, and their value can fluctuate based on market demand, rarity, and historical significance. The value of an NFT can also be influenced by the fame of the creator, as well as the quality and originality of the digital item.
NFTs also provide a new way for artists and creators to monetize their work and gain exposure. They offer a way for collectors to own and trade unique digital items that cannot be replicated.
Are NFT’s only artwork?
NFTs are not just limited to the art world. In fact, they can represent any unique digital asset that can be stored on a blockchain. This versatility has opened up new possibilities for various industries, including DeFi, or decentralized finance.
Some examples of NFTs that are not artwork include virtual real estate, music, sports memorabilia, tweets, and in-game items and experiences. NFTs can be used to represent ownership and authenticity of any digital item that is unique and has value.
In the context of DeFi, NFTs can also be used to represent LP (liquidity provider) positions on decentralized exchanges such as Uniswap. LP tokens represent a share in a liquidity pool that contains a certain amount of two different tokens. These LP tokens can be traded or sold on various platforms.
NFTs can be used to represent LP tokens, allowing users to trade and transfer their LP positions in a decentralized and secure way. This provides a new way for users to monetize their LP positions and participate in various yield farming and liquidity provision opportunities that exist on decentralized exchanges.

There are even NFT-based projects that are focused on LP positions and yield farming, such as Uniswap and Velodrome. These platforms allow users to trade and fractionalize their LP tokens, creating a new market for liquidity provision and yield farming strategies.
Overall, NFTs are a versatile and exciting technology that have the potential to revolutionize the way we think about ownership and value in various industries.
The future of NFTs
As the market for NFTs continues to grow, the potential applications and impact on the digital economy are vast. NFTs have the potential to revolutionize the art world, create new revenue streams for game developers, and provide a way for collectors to own and trade unique digital items. The gaming industry is particularly ripe for the growth of NFTs, with blockchain-based games and virtual worlds providing a new way for players to own and trade in-game items and experiences.
Conclusion:
The future of NFTs is exciting and full of potential. As the technology continues to evolve, we are likely to see even more innovative uses and applications of NFTs in various industries. From art and music to gaming and DeFi, NFTs offer a new way to own, trade, and monetize unique digital assets.
In the popular movie "Ready Player One," digital assets play a central role in the story's plot. The film envisions a future where digital currencies are used as a form of currency in a virtual world, where users can own and trade unique digital items and experiences. While this may seem like a far-fetched idea, it's not too far from reality. The gaming industry is already exploring the use of NFTs to represent in-game items and experiences, and the potential for NFTs to become a new form of currency is not too far-fetched.
In the context of "Ready Player One," the OASIS operates on a blockchain-like system, where users can buy, sell, and trade unique digital items. The rare Easter egg that Wade Watts is searching for is essentially a unique digital asset that grants ownership of the virtual world which is just like an NFT to show ownership of a particular digital asset.
As we look to the future of NFTs, it's important to stay informed and educated about the latest developments and potential applications. NFTs offer a new way to think about ownership and value in the digital realm, and they have the potential to disrupt various industries and create new opportunities for creators and collectors alike.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member RJ Ricasata.
Other CCE Committee articles:
Secure Your Crypto: A Guide to Different Wallet Types
Safeguarding Your Crypto Legacy: Best Practices for Cryptocurrency Inheritance Planning
Exchange/Custodial Wallet Pros and Cons
Additional Resources:
Prep Books (Digital Downloads)
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Introduction:
Cryptocurrency wallets are essential tools for managing and using digital assets. They provide a secure way to store private keys and interact with the blockchain to manage transactions and access funds. With the growing popularity of cryptocurrencies, there are now a wide variety of wallet types available, each with its own unique features and benefits.
In this guide, we will explore the different types of wallets, including hardware wallets, software wallets, and web wallets, to help you choose the right wallet for your needs. Whether you are a beginner just starting out with crypto, or an experienced user looking for a more secure solution, this guide will provide valuable information and insights.
In this guide we will briefly go over:
- Chrome Extension Wallets
- Web Wallets
- Mobile Wallets
- Desktop Wallets
- Hardware Wallets
- Open Source vs Closed Source Wallets
Please be advised that C4 neither endorses nor recommends any specific wallets that we discuss. Our content is intended solely for educational purposes to provide insights and information. We strongly encourage our readers to undertake comprehensive research and exercise due diligence. This will empower you to make informed decisions and select a wallet that is best suited to your individual needs and preferences.

A Chrome extension wallet is a type of cryptocurrency wallet that is accessed through a web browser extension designed for use with the Google Chrome web browser. It is a type of software wallet that allows users to store, manage, and access their digital assets through the Chrome browser. It is important to note that these extension based wallets also work on other similar browsers such as Brave, Firefox etc.
Chrome extension wallets offer the convenience of being accessible from any device with the Chrome browser installed. This means that users can access their wallet and manage their digital assets from any computer, laptop, or mobile device that has the Chrome browser installed.
In terms of security, Chrome extension wallets offer added protection because the user's private keys are stored locally on their device, rather than on a remote server like with a web wallet. This means that the user's funds are less vulnerable to hacking or other security breaches on the wallet provider's servers. However, it is still important for users to carefully research and choose a reputable wallet provider to ensure the security of their funds.
Some examples of Chrome extension wallets include:
- MetaMask: A popular Chrome extension wallet for Ethereum and other blockchains such as Polygon, RSK, Avalanche, BNB Chain among others as well as ERC-20 tokens on their respective chains.
- Rabby Wallet: A Chrome extension wallet for Ethereum and other based cryptocurrencies with a focus on user privacy and security.
Extension based wallets are a convenient and secure option for storing and managing cryptocurrency assets. However, like with all types of cryptocurrency wallets, it is important for users to understand the risks and take appropriate measures to protect their funds.

A web wallet is a type of cryptocurrency wallet that allows users to store, manage, and access their digital assets through a web-based interface. Unlike hardware wallets, which are physical devices that store cryptocurrencies, or software wallets, which are applications that run on a user's computer or mobile device, web wallets are hosted on remote servers and accessed through a web browser.
Web wallets offer the convenience of being accessible from any device with an internet connection, making them a popular choice for users who want to easily manage their digital assets from multiple devices. To use a web wallet, users simply need to create an account with a web wallet provider, deposit their digital assets into their online wallet, and then access their funds through the web interface.
In terms of security, web wallets are generally considered less secure than hardware or software wallets because the user's private keys are stored on the web wallet provider's servers. This means that users are reliant on the security measures of the wallet provider to protect their funds. As a result, it is important for users to carefully research and choose a reputable web wallet provider with a strong track record of security.
Some examples of web wallets include:
- Coinbase: A popular web wallet and cryptocurrency exchange with support for a variety of cryptocurrencies. Note, they have an extension based wallet, a custodial mobile, and non-custodial mobile wallet as well but Coinbase is best known for their exchange on the web.
- Binance: A web wallet and cryptocurrency exchange with support for a wide range of cryptocurrencies and trading options.
- Kraken: A web wallet and cryptocurrency exchange with support for a variety of cryptocurrencies and advanced trading features.
Web wallets offer a convenient and accessible way to manage digital assets, but come with some security risks. Users who are considering using a web wallet should carefully weigh the pros and cons, and take appropriate measures to protect their funds. Many of these wallets are custodial, which means that we do not own our keys, therefore, we do not have control and ownership of our cryptocurrencies. If you'd like to learn more on the pros and cons between custodial vs non-custodial wallets, check out our write up over here!

A mobile wallet is a type of cryptocurrency wallet that allows users to store, manage, and access their digital assets on a mobile device, such as a smartphone or tablet. Mobile wallets are specifically designed to be used on mobile devices and offer the convenience of being accessible from anywhere with an internet connection.
To use a mobile wallet, users need to download a mobile wallet app from the app store and install it on their mobile device. Once the app is installed, users can create an account and start using the wallet to manage their digital assets. Mobile wallet apps typically offer a range of features and functions, such as the ability to view balances, send and receive transactions, and track the performance of different digital assets.
In terms of security, mobile wallets offer some advantages over web wallets because the user's private keys are stored locally on their device, rather than on a remote server. However, they are still subject to the security risks of software wallets in general, such as the potential for malware or hacking attacks. It is important for users to carefully research and choose a reputable mobile wallet provider with a strong track record of security.
Some examples of mobile wallets include:
- Mycelium Wallet: A mobile wallet for Bitcoin and other cryptocurrencies with a focus on user privacy and security.
- BRD Wallet: A mobile wallet for a variety of cryptocurrencies with a focus on user-friendly design and accessibility.
- Trust Wallet: A mobile wallet for Ethereum and other ERC-20 tokens with support for decentralized applications (DApps).
- Exodus Wallet: A mobile wallet for a variety of cryptocurrencies with a focus on design and user experience.
- Edge Wallet: A mobile wallet for a variety of cryptocurrencies with a focus on user control, security, and privacy.
Mobile wallets offer a convenient and accessible way to manage digital assets on the go. However, like with all types of cryptocurrency wallets, it is important for users to understand the risks and take appropriate measures to protect their funds.

A desktop wallet is a type of cryptocurrency wallet that allows users to store, manage, and access their digital assets on a desktop computer. Desktop wallets are a type of software wallet that are specifically designed to be used for both desktop and laptop based computers and offer the convenience of being accessible from a single device.
To use a desktop wallet, users need to download and install the wallet software on their desktop or laptop computer. Once the software is installed, users can create an account and start using the wallet to manage their digital assets. Desktop wallet software typically offers a range of features and functions, such as the ability to view balances, send and receive transactions, and track the performance of different digital assets.
In terms of security, desktop wallets offer some advantages over web wallets because the user's private keys are stored locally on their device, rather than on a remote server. However, they are still subject to the security risks of software wallets in general, such as the potential for malware or hacking attacks. It is important for users to carefully research and choose a reputable desktop wallet provider with a strong track record of security.
- Electrum: A desktop wallet for Bitcoin and other cryptocurrencies with a focus on speed and security.
- Exodus Wallet: A desktop wallet for a variety of cryptocurrencies with a focus on design and user experience.
- Jaxx Wallet: A desktop wallet for a variety of cryptocurrencies with a focus on user-friendly design and accessibility.
- Atomic Wallet: A desktop wallet for a variety of cryptocurrencies with support for atomic swaps and decentralized trading.
- Armory Wallet: A desktop wallet for Bitcoin with a focus on advanced security features and cold storage options.
Desktop wallets offer a convenient and accessible way to manage digital assets on a single device. However, like with all types of cryptocurrency wallets, it is important for users to understand the risks and take appropriate measures to protect their funds.

A hardware wallet is a physical device that is designed to securely store your cryptocurrencies. It looks like a small USB drive and can be easily carried around with you. The idea behind a hardware wallet is that it enables you to store your cryptocurrencies offline, which makes it much more difficult for hackers to access your coins. This means that even if your computer or phone is compromised, your coins will remain safe on your hardware wallet. However, it is important to note that no form of storage is completely secure, and you should always take steps to protect your hardware wallet, such as keeping it in a safe place and not sharing your recovery phrase with anyone.
To use a hardware wallet, you will first need to buy one and set it up. Note, you will want to make sure you purchase this straight from the manufacturer as purchasing from a 3rd party could put you at risk with a tampered device. Once you have your hardware wallet, the next step typically involves connecting the hardware wallet to your computer or phone and following the instructions provided by the manufacturer to create a new wallet and generate a recovery phrase. Once your hardware wallet is set up, you can use it to store your cryptocurrencies by sending them to your hardware wallet's address.
Some examples of popular hardware wallets include:
These wallets support a wide range of cryptocurrencies and are known for their security and ease of use.
If you’d like to learn more about hardware wallets and security basics, click here.

The described wallets we went over can also be open source or closed source. Open source wallets and closed source wallets are two different types of cryptocurrency wallets that differ in terms of their source code and development approach.
Open source wallets are cryptocurrency wallets that have their source code publicly available and open for anyone to view, review, and contribute to. This means that the development of the wallet is transparent and decentralized, with contributions from a community of developers and users. Open source wallets are typically considered more secure and trustworthy because the code is open to scrutiny and audit by anyone, which can help identify and address potential vulnerabilities.
Closed source wallets, on the other hand, are cryptocurrency wallets that have their source code proprietary and not publicly available. This means that the development of the wallet is centralized and controlled by a single entity, such as a company or individual. Closed source wallets may offer more advanced features and functionality, but they also come with some security concerns because the code is not open to public review and audit.
Some examples of open source wallets include:
- Electrum: A lightweight, open source wallet for Bitcoin and other cryptocurrencies.
- MyEtherWallet: An open source wallet focused for Ethereum and other ERC-20 tokens.
- Wasabi Wallet: An open source wallet for Bitcoin with a focus on privacy and anonymity.
- ZenGo: An open source wallet for a variety of cryptocurrencies with a focus on user-friendly design.
- Edge Wallet: An open source wallet for a variety of cryptocurrencies with a focus on user control and privacy.
The choice between open source and closed source wallets ultimately depends on the individual user's priorities and needs. Users who value security and transparency may prefer open source wallets, while users who value advanced features and functionality may prefer closed source wallets.
There are some wallet projects that have different variants such as mobile wallets, desktop wallets and connection with hardware wallets. One of them is Green Wallet, exclusive for Bitcoin and the liquid network (second layer of bitcoin). Green Wallet is also open source.
Closing:
In conclusion, cryptocurrency wallets are essential tools for managing and using digital assets. They provide a secure way to store private keys and interact with the blockchain to manage transactions and access funds. With the growing popularity of cryptocurrencies, there are now a wide variety of wallet types available, each with its own unique features and benefits.
In this guide, we have explored the different types of wallets, including hardware wallets, software wallets, and web wallets. We have discussed the key features and differences of each wallet type, as well as the pros and cons of open source and closed source wallets.
Ultimately, the right wallet for you will depend on your specific needs and priorities. Whether you are a beginner just starting out with crypto, or an experienced user looking for a more secure solution, it is important to carefully research and choose the right wallet for your needs. By understanding the different types of wallets and their features, you can make an informed decision and take steps to secure your crypto assets.
If you need help deciding what wallet might be right for you and are not sure, you can also visit https://bitcoin.org/en/choose-your-wallet and answer the questions which can guide you to select one based on your preferences and priorities.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member RJ Raljoseph Ricasata.
Other CCE Committee articles:
Self Custody Wallet Pros and Cons
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Overview
Cryptocurrencies offer the ability to send secure, irreversible payments to any person anywhere in the world. These borderless technologies are powerful tools for payments — but with this comes power scammers can use to steal, leaving victims with no way to get their money back. There are several common types of crypto scams that any user may encounter. Let’s look at these types of scams and ways to prevent losing money to them.
Types of Scams
Investment Scams
One of the most common scams in the crypto space is the fraudulent “investment” scam. In this type of attack, the thieves trick users into believing they are investing in a lucrative opportunity. In reality, the victim is simply sending cryptocurrency to the scammer’s wallet.
These scams most often start via social media. The perpetrators create convincing profiles of fake “investment managers” that appear to be rich. The name isn’t always a good indicator, but many accounts have “trade” or “fx” (short for foreign exchange) in the name. The accounts have stories or pictures of fake “user withdraws” and fancy cars/houses/lifestyle items to draw you in. The returns promised are too-good-to-be-true, often upwards of 10% per day — this is a red flag.
These scams may also tie-in with impersonation scams, where someone pretends to be a famous person (often related to cryptocurrency) to steal your money. For example, someone pretends to be Andreas Antonopoulos, Roger Ver, or another noteworthy individual.
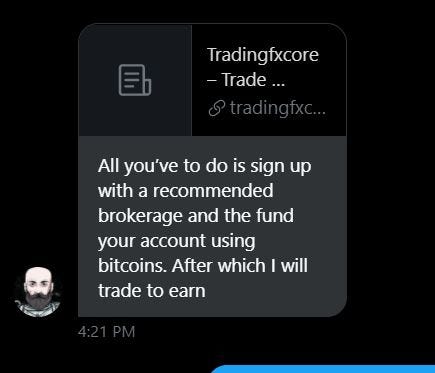
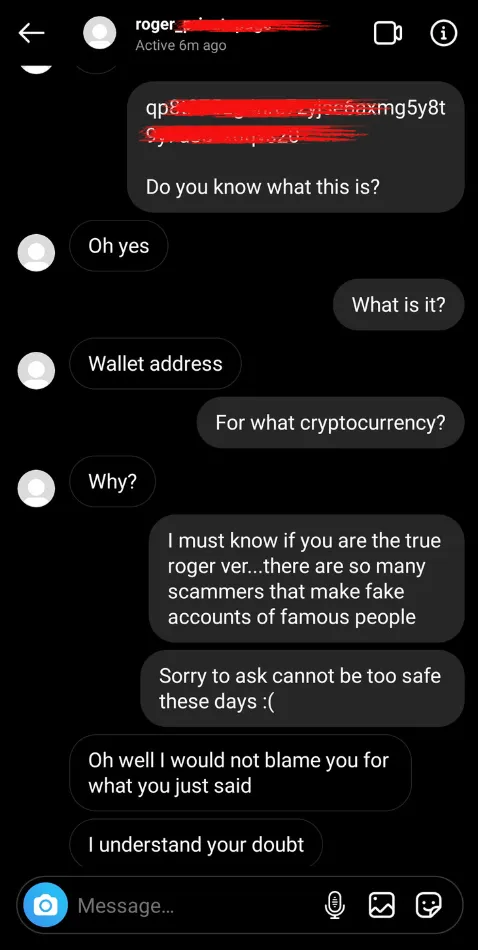
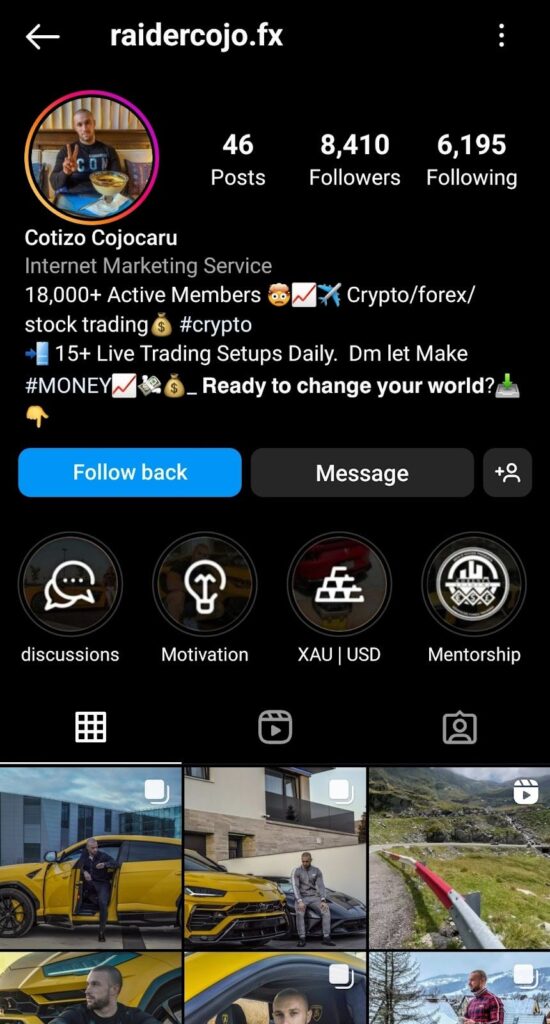


The scammers will initiate a conversation with you unprompted, and lead you to a fake but convincing “trading” website that asks for deposits in cryptocurrency, usually Bitcoin or Ethereum. The website may feature account balances, price information, investment packages, or other information designed to make it appear to be legitimate. They may even have fake but convincing press releases or certifications that make them seem real.
Ultimately, the website and account manager are just a ruse to trick you into thinking you’re involved with a real investment. In reality, you’re simply sending crypto to the scammer’s wallet. These attacks take advantage of crypto’s irreversible nature. Once you send coins to the scammers, you have no ability to get it back. They will often try and convince you into sending more and more money to pay for “taxes” and “withdrawal” fees.
A similar form of the investment scam is the “Cloud Mining” scam. In this variation, scammers ask you to invest money to pay for mining equipment, which the scammers claim will generate returns for you. Just like the typical trading investment scam, cloud mining is all a facade. There is no real mining that happens, and the scammers keep the cryptocurrency you sent to them.
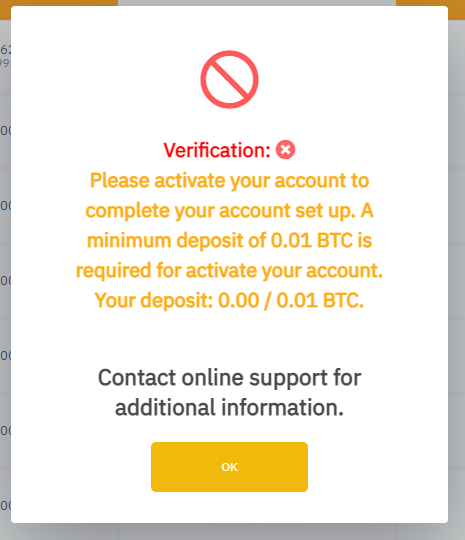
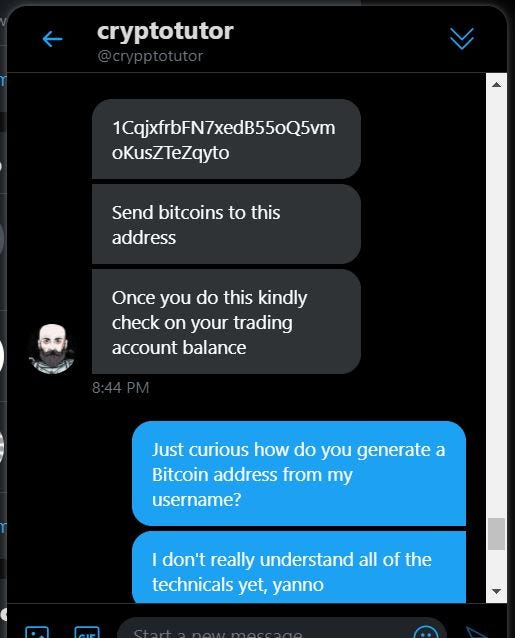
Prevention
You should never send cryptocurrency to anyone pretending to be an investment manager. Only hold cryptocurrency in your own wallets such as a hardware wallet for long term storage. If you wish to store coins with a custodian, stick with well known and vetted exchanges. Understand that cloud mining is not a profitable venture, if not an outright scam. Do a few thorough web searches on any potential platform. Others may have already been scammed and shared a warning on forums, or there may be red flags such as brand-new websites.
Be wary of anyone promising too-good-to-be-true returns, and understand that platforms such as crypto lenders/earning services are substantially more risky than simply holding coins yourself.
Recovery Scams
Sadly, many victims of investment scams fall victim a second time to recovery scams. Once a cryptocurrency transaction is sent and confirmed on the blockchain, there is no way to reverse that payment. Regardless, many victims are desperate to get their money back after losing it to a scam.
Recovery scammers work by pretending to offer legitimate recovery services, all while tricking users out of more money and accounts. A recovery scammer pretends to have some special technical knowledge or “hack” for retrieving stolen coins, and will offer to do so for a fee. While in the process of your fake “recovery”, the attacker will often steal credentials for exchange accounts or seed phrases so they can clean them out.
These are usually advertised by bots in the comment section of a post or other social media interaction that mentions a scam or technical problem with a wallet. Bots look for certain keywords and then post links or names of the fake recovery scammers.
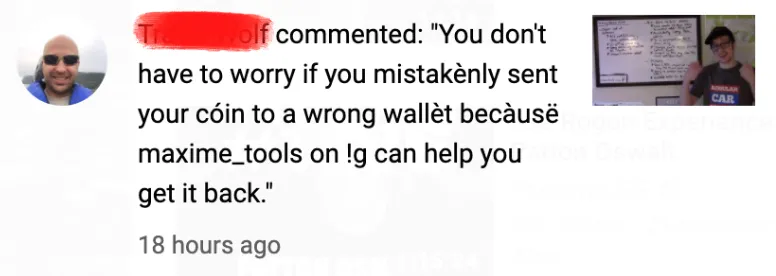
Prevention
First, understand that cryptocurrency transactions are irreversible. Always double, triple check addresses before sending coins to anyone and be sure the wallet you’re sending to is for a legitimate purpose (such as paying for goods or services). Never send coins to someone claiming they can do the impossible — reverse a transaction. Never give seed phrases, 2FA codes, or passwords to anyone else, even if they claim they are trying to help you.
Phishing Scams
Phishing is one of the most common ways that attackers steal cryptocurrency. In many cases, it is easier to break people than it is to break technology. In other words, tricking you into sending coins, a seed phrase, or another means of stealing your money is easier than hacking a well-designed wallet to steal keys.
These often take the form of seed phrase phishing. A 12–24 word seed phrase grants access to all the coins in a crypto wallet. This is a powerful backup tool, but is also a great target for thieves. Phishing may take the form of an email from a wallet, claiming that you have to “verify” your wallet within 24 hours or your account will be locked. This is a ruse, as you cannot “lock out” a self-custody crypto wallet. This email leads to a form that steals your seed words.
Phishing websites are often sophisticated and very real looking. For example, the real Edge Wallet exists only as a mobile application. And yet, there exist convincing phishing clones like edgewallet.io that steal credentials from the users of the real wallet. These fake platforms can even appear high in search results.
There are also types of computer viruses that replace a copy-pasted address with that of a scammer’s. For example, you copy an address from Coinbase. When you paste it, the software replaces it with the scammer’s. If you don’t double-triple check the address, you inadvertently send it to the thieves.
Prevention
It’s important that you never, ever give your seed phrase to any other person. When entering a backup phrase to restore a wallet, make sure you’re only entering it into the wallet software you intend to use. For example, use a Coinomi seed phrase with a Coinomi or Exodus wallet downloaded from the app store. If it’s a hardware wallet, only enter the seed on the device itself — never into a computer or phone. When sending coins, be sure to double-triple check the address you’ve entered is correct and belongs to the intended recipient. Once coins are sent, there’s no way to reverse the payment.
Giveaway Scams
Who doesn’t love free money? Most of us do! The final type of scam in this article will discuss the giveaway scam. Giveaway or “Doubling” scams trick a user into sending coins to a scammer’s address with the promise of an airdrop or free cryptocurrency in return.
These usually use the image of rich and famous people or organizations to lend legitimacy to the scam. Sometimes the legitimate accounts of these people are hacked/stolen to promote scams. In one example, the MMA organization the UFC had their YouTube account compromised and used to promote a scam.
Fake airdrop scams operate similarly to investment scams with a slightly different angle. Instead of asking you for cryptocurrency to “verify” your address, these fake airdrop platforms promise free tokens by connecting your wallet to the website. For example, by using WalletConnect, a seed phrase, or a browser wallet extension such as MetaMask. The website then uses those permissions to steal all of your coins and tokens. Remember, there is no such thing as free money!
Prevention
Never send cryptocurrency to anyone with the promise of a return. Cryptocurrency transactions are irreversible, so if you send coins to a scammer there is no way to get them back. Never connect to a website using WalletConnect or MetaMask with the promise of an airdrop, as this can be used to steal your funds. As well, cryptocurrencies use public key cryptography. Your address is safe to share, and nobody can use only your address to steal coins. If someone truly wants to give you crypto for free, you only have to give them your public address.
Avoiding Scams
In general, most scams start with a too-good-to-be-true promise. Either a lucrative investment opportunity, or a chance at a giveaway, or even the possibility of returning lost coins. Always ask yourself if something sounds too good to be true before getting involved. As well, always understand that cryptocurrency transactions are irreversible — once coins are sent there is no way to get them back. Take your time before sending, before entering a seed phrase anywhere but a wallet, or interacting with others on social media.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Online security is not a luxury but an essential aspect of our digital lives. Understanding the basics of protecting our sensitive information and digital assets empowers us to navigate the online landscape with confidence.
From managing finances to sharing personal information, it's crucial to adopt best practices for online security. By following a few simple guidelines, you can protect yourself from cyber threats and enjoy a safer online experience.
Let's dive in!
Create Strong and Unique Passwords:
One of the fundamental steps in securing your online presence is to create strong and unique passwords. Avoid using obvious choices like "123456" or "password." Instead, create complex passwords by combining uppercase and lowercase letters, numbers, and special characters. Furthermore, refrain from reusing passwords across multiple accounts. Consider using a password manager such as 1password, NordPass or Keeper, to securely store and generate strong passwords for you.
While passwords should be complex, length is a more important factor than just additional numbers and symbols. An 8 character password with uppercase, lowercase, numerical, and special characters can still be cracked in minutes to hours. Whereas, a 16 character random password with just uppercase, lowercase, and numerical characters can take millions of years to crack. The time it takes to brute-force guess passwords increases *exponentially* with each additional character, but doesn't increase much by increasing the character set.
Enable Two-Factor Authentication (2FA):
Two-factor authentication provides an additional layer of security by requiring an extra verification step, typically a unique code sent to your mobile device, in addition to your password.
Enable 2FA whenever available, especially for critical accounts like email, banking, and social media. This added security measure significantly reduces the risk of unauthorized access to your accounts.
There are multiple types of 2FA; wherever possible, use the best available type of 2FA for your account.
Authenticator app or hardware security key 2FA, offer less potential avenues for compromise, outside of stealing the device itself. A hardware security key is a device, similar to a USB stick, that offers extra security for online accounts. Used with a password, it's part of two-factor authentication (2FA). Like a house key, even if someone knows your password or address, they can't access without this physical key.
Authenticator app (auth-app) based 2FA (Microsoft, Google, Duo, etc.) provide a greater level of security than SMS (text message) or email based 2FA. SMS 2FA is vulnerable to "sim swap" attacks, where the attacker tricks the phone company into porting your number onto their phone (so they can then steal your accounts).
2FA is "something you have" where the password is "something you know". These offer additional layers of security than simply having the password, because an attacker must now compromise both layers to steal the account.
Keep Your Software and Devices Updated:
Regularly updating your devices, operating systems, and software applications is vital for online security. These updates often include important security patches that address vulnerabilities and protect against emerging threats. Enable automatic updates or set reminders to ensure you're always running the latest versions.
Be Vigilant against Phishing Attempts:
Phishing attacks continue to be a prevalent threat. Exercise caution when interacting with emails, messages, or pop-ups requesting personal or financial information. Be skeptical of suspicious links or attachments, and avoid providing sensitive data through unsecured channels. Verify the legitimacy of requests by contacting the organization directly through official channels.
Phishing attacks can be sophisticated or simple. Always be vigilant if someone is asking for information such as wallet seed phrases, passwords, or 2FA tokens. If you receive an email, text or other communication asking for information, go directly to the website in question instead of following links provided in the message. For example, if you receive an email about KYC verification from someone claiming to be Coinbase, don't follow the link in the email. Go directly to Coinbase.com to log in and see if the request is legitimate.
Never give out a seed phrase for a cryptocurrency wallet, no matter why someone claims they need it. Only enter your seed into a piece of wallet software you want to use. Even then, be vigilant and ensure the software is legitimate. Anyone with your seed phrase has *full access* to all of the money in that wallet.
Utilize Secure Wi-Fi Networks:
Public Wi-Fi networks are convenient but often lack adequate security measures. Avoid accessing sensitive information, such as online banking or shopping, when connected to public Wi-Fi. If you must use public networks, consider using a virtual private network (VPN) to encrypt your data and protect your privacy. Most critical websites such as online banking will use Hypertext Transfer Protocol Secure (HTTPS), which offers a layer of encryption between you and the website. It is helpful to ensure websites you use always use HTTPS, especially if you use them to "log in" via a password.
Practice Safe Online Shopping:
Online shopping offers convenience, but it also presents potential risks. Stick to reputable websites and ensure they have secure connections (look for "https://" and a padlock icon in the address bar). Avoid making purchases on public computers or using public Wi-Fi networks. Regularly review your credit card and bank statements for any suspicious activity.
Protect Your Personal Information:
Be cautious about sharing personal information online. Avoid posting sensitive details, such as your full address, phone number, or financial information, on public forums or social media platforms. Adjust privacy settings on social media to limit who can access your personal information, and be mindful of what you share with third-party apps or services.
Regularly Back Up Your Data:
Data loss can occur due to various reasons, including cyber attacks, hardware failure, or accidental deletion. Regularly backup your important files and documents to an external hard drive, cloud storage, or both. This ensures that even if something unexpected happens, your data remains safe and recoverable.
Backups should follow the "3-2-1" rule: 3 copies of the data in total, 2 different types of media, and 1 offsite backup. So for example: one copy on your PC solid state drive, one copy in "cloud storage", and another on an external hard drive.
Educate Yourself about Online Threats:
Staying informed about the latest online threats and security best practices is essential. Keep yourself updated on common scams, new hacking techniques, and emerging vulnerabilities. Follow reputable online security blogs or subscribe to newsletters from trusted sources to stay informed and better protect yourself.
Invest in Reliable Security Software:
Equip your devices with reputable antivirus and anti-malware software. Ensure these programs are up to date and regularly perform scans.
Conclusion
By adopting strong passwords, recognizing phishing attempts, and staying updated on security practices, we strengthen our defenses against ever-evolving cyber threats.
Whether for individuals or businesses, online security is the key to safeguarding our financial well-being, personal privacy, and online reputation and embracing this responsibility ensures that we can fully enjoy the boundless opportunities of the digital age while minimizing the risks.
So, let us commit to being informed and proactive, creating a safer digital environment for ourselves and future generations.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Michelle Demarest and Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Why Have a Plan?
Your digital assets should be treated like any other personal property when estate planning, and it is important that you take steps to include them in your Will. However, the assets will only be available to your heirs if you have developed a plan. That plan should include detailed instructions for them about what you have and how to access it.
Where Do I Start?
Before diving into inheritance planning, make sure you have a solid understanding of cryptocurrencies. Use trusted sources, such as C4, to familiarize yourself with the basics of blockchain technology, private keys, wallets, and the specific cryptocurrencies you hold. This knowledge will empower you to make informed decisions and communicate effectively with your beneficiaries.
Start Simple:
Although it may seem overwhelming, start with a simple pen and paper to create an inventory of your assets. There are templates available online that can be printed off, filled out, and stored in a safety deposit box or in a secure location in your home.
You can also to explore the growing number of cryptocurrency estate planning tools and services available. These tools can assist you in securely storing and transferring your digital assets.
They often offer features such as multi-signature wallets, time-locked transactions, and contingency plans for managing your cryptocurrencies in specific circumstances.
Pamela Morgan’s book “CryptoAsset Inheritance Planning: A Simple Guide for Owners”, has templates to help get you started and offers additional guidance as you develop your plan. (Disclosure: Pamela is a board member at C4.)
Regardless of where or how you start, we urge you to use the knowledge provided in this article to further educate yourself with the plan and options that best suit your needs and situation. Unlike other assets, there is no ‘Bank Manager’ and not having a plan could almost certainly guarantee some or all of your crypto assets may be lost when you’re gone.
In general, a balance of both legal and technical assistance will help ensure your assets can be properly passed down to your loved ones, while still keeping them secure.
Here are some general best practices to get you started with a simple inventory to help with the creation of your cryptocurrency inheritance plan.
Inventory Planning:
Start by creating an inventory of all your cryptocurrency holdings. Include information such as the name of the cryptocurrency, wallet addresses, private keys, and any relevant account information. Keep this inventory updated as you acquire or sell cryptocurrencies. You may also want to include information relating to:
- Exchanges — Write down the exchanges you are currently using or have used in the past. Do not list your password or login credentials at this stage.
- Wallets — If you use a wallet hosted by an exchange, note which wallet is connected to which exchange in the step above. If you are holding your own keys, then your heirs should be made aware of at least two things: Name(s) of the wallets you use and where your wallet backups are located. Remember, anyone who has access to these backups could steal the funds. Be aware of this when considering anyone that may be assisting you or has access to your plan.
- Devices — List the devices that you are using to access your wallet accounts, such as your phone or laptop. This will ensure your heirs know not to throw away, donate, gift, or destroy these devices until the funds have been successfully retrieved/moved. It is good to note that you do not need to provide your passwords for these devices at this stage. A picture may also be beneficial to ensure they know the devices they are looking for (i.e., a generic photo of your hardware wallet model).
Consider Wallet Seed Storage
Your wallet seed is a combination of random words that enable you to access your cryptocurrency on the blockchain in case you lose access to your wallet. It is recommended to store your wallet seed using an element proof device, such as a steel wallet.

Don’t Overcomplicate:
In order to make sure that your loved ones understand your cryptocurrency holdings and how to access them, provide clear instructions on where to find the inventory, how to access wallets, and any necessary passwords or recovery phrases. It’s crucial to communicate your intentions and wishes regarding the distribution or management of your cryptocurrencies.
At a minimum, it is best to avoid unnecessary costs and it should not take years for your heirs to follow the ‘clues’ to uncover where your more detailed plan is stored or solve a riddle to determine where you have hidden all the diversely distributed portions of your seed.
Don’t overestimate the technical ability of your heirs.
Define Support for your Heirs:
It is recommended at minimum, your heirs know 3 main areas: Exchanges, Wallets, and Devices.
Identifying helpers/individuals your heirs can go to for assistance is a good option to avoid your inheritors going to untrusted sources, such as the Internet, for help. Identifying people who might be able to assist doesn’t mean, however, that you give them your passwords or keys. These helpers will simply be people that your beneficiary(s) can contact to help direct them with the proper asset retrieval.
Consider people you trust to help and simply list them at this stage.
As you develop your plan, it may be prudent to provide your helpers with trustworthy resources, where they can access content that focuses on helping crypto — C4’s CCE content is always a great place to start.
Take a First Step:
Ultimately, without a plan, your heirs may not be able to access or retrieve your cryptocurrency holdings. This first step should assist you in building a more comprehensive plan, especially if you’re holding a large amount of cryptocurrency. Remember, planning for distribution of your cryptocurrency assets will take time and should be included in a will, testament, or legal trust.
We recommend you also take the time to educate yourself and consult with legal and financial professionals to develop a robust and secure cryptocurrency inheritance plan.
Safeguard your crypto legacy and leave a lasting digital footprint for future generations.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Michelle Demarest.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Overview
Cryptocurrency exchanges serve as convenient on and off ramps for users. These services allow people to trade fiat currency (such as dollars, euros, or yen) for cryptocurrencies, or to trade between various digital assets. These exchanges often serve a second function — as custodial wallets. Most major exchanges will allow users to store digital asset balances, and send/receive them on the blockchain. There are a number of pros and cons to storing digital assets on custodial exchanges.
Pros of Custodial Wallets
The major pro of using custodial wallets is simply ease-of-use. There are several advantages to storing and using cryptocurrencies via exchanges when it comes to the user experience.
The first is that the security experience is familiar for most users. Custodial wallets feature username and password based logins with 2 factor authentication. This login experience is the same as many other popular web applications such as social media sites, email, and bank accounts. Familiarity with security practices increases the likelihood users will avoid costly mistakes, especially when new to a domain like cryptocurrency.
As well, using an exchange wallet offers all functions cryptocurrency users might want “under one roof” — they can buy and sell, trade currencies, and send and receive to external wallets. This can make tasks such as inheritance planning, transfers, and interfacing with legacy financial instruments easier.
A final advantage of exchanges/custodial wallets can be support and documentation. Exchanges are businesses, and often have dedicated support staff and quality documentation. These resources can help both new and experienced users navigate security challenges.
Cons of Custodial Wallets
Custodial wallets do have several disadvantages to self-custody solutions. The most notable is that custodial wallets reintroduce counterparty risk into the cryptocurrency experience. Counterparty risk means, simply, having to trust a third party with your cryptocurrency assets. One major advantage of cryptocurrencies is the ability to hold your own keys and therefore your own money without having to trust someone else.
Using an exchange to store assets is more similar to trusting a bank, but with less regulations and safeguards. Users are exposed to several threats — such as insolvency. Several major custodial exchanges in cryptocurrency history have dissolved or filed for bankruptcy, such as Mt.Gox, QuadrigaCX, and most recently, FTX. Exchanges also serve as large, centralized targets for hacks and theft. While many major exchanges have excellent security practices, there is always the possibility of compromise. And large repositories of user funds like an exchange are a larger potential target than individual users.
While the familiar security user experience of exchanges can be an advantage, it can also be a disadvantage if a user has poor security hygiene. If a user generates a poor quality, short, or reused password, their account may be compromised easily. Similarly, poor 2 factor authentication practices such as using SMS may lead to SIM-swap attacks and account takeover. Users that neglect their email security may find it used to initiate password resets and account takeovers.
You can learn more about cryptocurrency security by visiting https://cryptoconsortium.org/articles.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Overview
Cryptocurrency exchanges are a vital part of the ecosystem, as they allow users to buy and sell various coins and tokens for common currencies such as the US dollar. Exchanges also serve as an entry-level wallet without having to understand seed phrases and other self-custody security procedures. While exchanges are an important part of the decentralized ecosystem, most themselves are centralized, meaning they control your private keys on your behalf. Exchanges come with their own security best-practices users should follow to keep their assets safe.
Password Management
Users should first focus on password hygiene when thinking of exchange security. There are 3 areas of focus for password security - password length/complexity, password reuse, and password storage.
The first rule to follow is do not reuse passwords, especially for cryptocurrency exchange accounts. The password for your account must be unique. This prevents password leaks from other services from compromising your exchange account. For example - let's say you reuse the same password for your exchange account and for an online shop. If the online shop's password database is compromised, attackers may try and use that password to gain access to your account. This type of attack is known as credential stuffing.
The second security practice is to favor length over complexity when generating your passphrases. Many think that adding additional characters to a short password makes it harder to crack - for example changing the password LeetSpeak to L33t$pe@k. However, this does not significantly increase the time it takes an attacker to guess your password! In fact, length is far more important than special characters. For example - ILikeToCreateLongerPassphrases is far more secure than L33t$spe@k.
The most difficult passwords to crack are those generated from secure random sources. Even better than ILikeToCreateLongPassphrases is something like e9623WR108SpXSbfhSlj. This passphrase contains a high amount of entropy (randomness). If your password needs to be typed rather than copy/pasted or autofilled, diceware passphrases can be generated using wordlists and random sources like dice or a diceware password generation tool. For example: JeanRemanTonCockyTyburn. These are English words that have no correlation with each other, but are easy to type or even remember if necessary. A complex and hard-to-crack password does not necessarily have to be difficult. Combining 5 unrelated words that you can remember is a good first step towards creating a strong passphrase.
A third challenge users face is storing and remembering all these long, randomly generated, unique passphrases. Many users have tens if not hundreds of online accounts. To prevent password reuse, or having to remember high-entropy passphrases, a password manager is an excellent security tool. Password managers store passphrases in an encrypted database - the user only has to remember one very long and secure master passphrase to access the manager. Most modern password managers make it easy to autofill passphrases into websites, or to copy/paste them as needed. Most will also generate high entropy passwords for you.
2 Factor Authentication
It's also critical that users apply strong 2 factor authentication (2FA) to their exchange accounts. This adds a second layer between an attacker and account access. A password is "something you know", while most 2FA tokens are "something you have." There are 3 common types of 2FA.
The first is email or SMS text-message based. In this case, after entering your passphrase, the website sends you a one-time code via email or text. You enter the code into the website to finish logging in. This type of 2FA is strongly discouraged - because it is the easiest for an attacker to steal from you. Many in the cryptocurrency space have lost accounts and assets via SIM swap attacks - where the attacker pretends to be you, calls the phone company, and ports your number to their phone. They can then use the 2 factor codes to take over the exchange account.
A second more secure method is to use app-based 2FA via apps like Microsoft Authenticator, Google Authenticator, Duo, and many other examples. For app-based 2FA, you first set up authentication by installing an app on your phone and scanning a "seed" provided by your account. The app on your phone then generates one-time codes that change every 30 seconds or so. You enter these codes into the website to complete logging in, just as with SMS based. However, the codes are generated from a secure seed stored by the app instead of transmitted over text messages which is far more difficult to steal.
The third and most secure type of common 2FA is hardware security token-based. A popular example is the Yubikey brand of hardware devices. These are small USB sticks that can be linked to your account. When logging in, you simply make sure your token device is plugged into the PC you are using. Compromising this type of 2FA requires physically stealing a user's device which is an uncommon form of attack (compared to SIM-swapping).
Email Security
Many users overlook email security when considering the security of their exchange accounts. Most often, access to email allows a legitimate user to "password reset" the account in case they forget their passphrase. If your email is insecure, an attacker could first gain access to your email and then use it to take over your crypto exchange account. You should ensure you follow the same best practices for email - strong, unique passphrases and app or hardware-based 2FA. It may also be helpful to use a separate email just for cryptocurrency-related accounts, following all of these security guidelines around securing that account. This may prevent someone from easily obtaining your email as a first step to account compromise.
You can learn more about cryptocurrency security by visiting https://cryptoconsortium.org/articles.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Overview
One of the core components of blockchain technology is the concept of “private keys” which may be viewed as the mechanism to authorize a transaction on the blockchain. One of the fundamental decisions one must make is who is in control, or custodying, those keys. One may choose to have a trusted third-party custody those keys or one may choose to safeguard those keys themselves, or self-custody. Self-custody in the context of cryptocurrency means “the user holds their own private keys”. There are many ways a user can safeguard these keys, such as a mobile wallet on your mobile phone, a wallet application on your desktop, or a special hardware device known as a hardware wallet. One of the challenges relates to how to backup these private keys in a manner that is convenient as well as secure. When a user generates a new mobile wallet or hardware wallet, for example, they are given a “seed phrase” to back up. The seed phrase, typically 12 or 24 random words, is a mechanism used in many modern wallets to use as a foundation in which other keys may be generated from. This convenience results in only needing to backup and safeguard that seed phrase since that seed can be used to regenerate the same keys. This approach is powerful, with several security advantages over custodial solutions providing it’s done in a safe and secure manner. There are, however, some disadvantages to self-custody. Let’s dive into the pros and cons of managing your own crypto keys.
Pros of Self-Custody Wallets
The first major pro of self-custody is self-sovereignty — part of why crypto exists is so that users can truly own their digital money by holding their own keys, rather than having to trust a third party with your keys as well as your private information. Having to trust a third party is known as “counterparty risk”. This method transfers the responsibility of safeguarding those keys to that other party and you are now relying on their security. By holding one’s own keys, a cryptocurrency user avoids counterparty risk in their key ownership.
A second advantage is that of options. There exists a multitude of cryptocurrency wallets for every level of security, technical knowledge, or desired currencies and tokens. Depending on the user’s desired level of security, one could use a simple mobile wallet or go all the way up to a hardware wallet or even utilize more complex configurations such as requiring multi-signature. Moreover, many popular wallets are open source and audited by the professional development and security community, and closed source wallets have strong user bases as well with many offering a bug bounty program to reward ethical hackers who find vulnerabilities.
It is also easy to move between self-custody wallets — there is no concern of lock-outs, know your customer regulations (KYC). There are often more supported cryptocurrencies available, as new tokens or currencies that aren’t yet available on exchanges can be used via self-custody software.
These wallets offer the highest level of accessibility for all around the world. A user only needs to install wallet software on a mobile phone to start transacting with cryptocurrency. There is no need for identification, a bank account, or addresses to use a simple self-custody wallet. This is a huge advantage for those without access to traditional banking services.
Cons
There are, however, some disadvantages of self-custody wallets over custody accounts. Most of these revolve around backups and issues of security hygiene. First, a user must take sole responsibility for the safeguarding of their keys, and therefore their money. If the user loses their wallet (such as their phone), and loses backups of their seed phrase, they will lose access to their coins with no options for recovery.
The user must exercise diligence in securely backing up their seed phrase (private keys) and maintaining access to those backups. These should be stored in multiple secure locations and tested to ensure recovery works if the primary wallet is lost. If a backup is made or stored improperly, the user can lose access to their coins.
Every user of a self-custody wallet must take ownership of their security — both digitally and physically.
You can learn more about types of wallets and custody by visiting https://cryptoconsortium.org/articles.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Bitcoin Pizza Day is an annual event celebrated by Bitcoiners on May 22nd every year. Bitcoin Pizza Day commemorates the first documented real-world transaction using bitcoin. This transaction is historically significant in the development and adoption of cryptocurrencies. Plus, what’s better than pizza plus decentralized finance?!
On May 22, 2010, a programmer named Laszlo Hanyecz posted on a Bitcoin forum, offering 10,000 bitcoin to anyone who would deliver him two pizzas. At that time, bitcoin was a relatively new concept, and its value was extremely low. Jeremy Sturdivant responded to Laszlo’s offer and agreed to the transaction.

Sturdivant ordered two pizzas from Papa John’s using traditional fiat currency and had them delivered to Laszlo’s doorstep. In return, Laszlo sent 10,000 bitcoin to Jeremy, completing the first-ever recorded purchase using bitcoin as a medium of exchange.
Sturdivant has said he is “proud to have played a part” in the “global phenomenon” of bitcoin. We’re certainly glad he thought outside the ‘pizza’ box!
So, why does Bitcoin Pizza Day matter?
It demonstrates the early adoption and real-world application of bitcoin. Laszlo’s purchase showed that bitcoin had potential beyond being a theoretical digital currency. It highlighted the ability to use bitcoin as a means of conducting everyday transactions. Plus, what a delicious first transaction!
Bitcoin Pizza Day has become a symbolic event in the cryptocurrency community for the past 13 years. It reminds enthusiasts of the journey bitcoin has undertaken, from its humble beginnings to becoming a prominent global digital currency. The celebration showcases the progress and wider acceptance of cryptocurrencies, fostering a sense of community and appreciation for the technology behind them.
Overall, Bitcoin Pizza Day is a playful and meaningful annual celebration that serves as a reminder of the innovative possibilities that digital currencies offer.
This is one cheesy party you won’t want to miss!
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

A Beginners Guide to Cryptocurrency Wallets
Before we discuss types of wallets, it is a good idea to first have a general understanding of what cryptocurrency is and why it is important.
Many cryptocurrencies work by utilizing public networks and ledgers (a ledger is a record of financial transactions) called blockchains. At its simplest level, cryptocurrencies let you send and receive value to and from anyone in the world, using only an Internet connection. What makes it so revolutionary is that, unlike every other tool for sending money over the Internet, it works without the need to trust or gain the permission of a centralized authority. Which makes it the world’s first public and decentralized digital payments infrastructure!
Public in this case, means no single entity owns or controls the ledger, nor can it be changed. This decentralized ledger reduces the risk for corruption, fraud and manipulation and decreases time, cost and limitations associated with the use of such entities.
Feeling confused? Don’t worry, we will provide additional content to help you understand this technology. For now, this is enough to set the framework for this wonderful, and sometimes weird, journey!
How Do I Get Started?
As mentioned above, cryptocurrencies use blockchain technology. All that is needed is an address on the Blockchain to receive payments digitally.
Given this, the first step to starting your cryptocurrency journey will be to choose and set-up a wallet, which will create an address on your chosen blockchain.
What is a wallet and why exactly do I need one? Let’s start with the why.
Why Do I Need a Wallet?
Just like you need an email application like Outlook or Gmail to manage your email, you need a cryptocurrency wallet to manage your cryptocurrency. Wallets monitor addresses on the blockchain and even update their own balance with each transaction.
An address is like your email address. It is something you provide to people who want to send you cryptocurrency.
Now that you know the why, let’s talk a bit about the how.
How Does a Wallet Work?
A cryptocurrency wallet, is an application with 3 main functions:
- Send and receive cryptocurrency
- Store cryptocurrency
- Monitor cryptocurrency balances
One of the most important things to remember about a wallet, is that this is where your private key is stored. In essence, a private key is just a very long string of numbers and letters that act as the password to your wallet.
You might be asking yourself, what are keys? Keys control access to your wallet.
There are 2 key types: private keys and public keys.
A public key is a unique code that acts like a digital address for your cryptocurrency wallet. It’s used to receive funds from other wallets. Similar to a bank account number, where it can be shared with others and money can be deposited into, but will not provide the sender access to your bank account.
You will typically be asked to generate a new public and private key pair, and the public key will be displayed as your wallet’s “receiving address.”

Private keys can be compared to your bank password that gives you access to authorize withdrawals. Because your private keys provide you with access to your cryptocurrency, they should never be shared with others or put online. Just like your online banking password, the private key is to be seen only by the person who owns the address to keep your currency safe.
We want to emphasize this statement. Just like your online banking password, your private key(s) should never be shared with anyone.
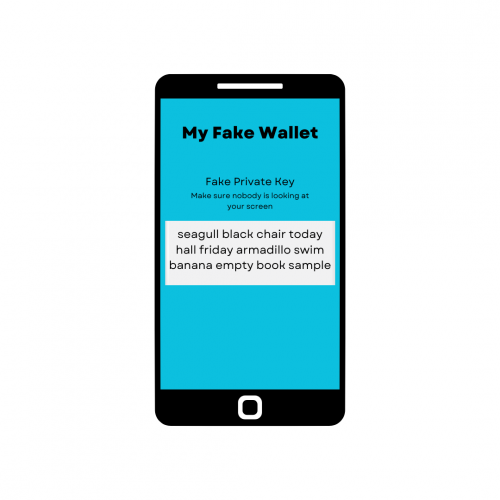
Wallet Categories
There are different wallets, and the type of wallet/s you use to hold your crypto will vary depending on your needs.
For this article, our goal is to provide a general understanding to help you recognize there are different types of wallets. So don’t worry if this leaves you a bit confused. We are here to help and in follow-up articles, we will provide additional content digging deeper into each one.
Let’s start with names of the most common wallet types:
- Chrome Extension Wallets
- Web Wallets
- Mobile Wallets
- Desktop Wallets
- Hardware Wallets
- Open Source vs Closed Source Wallets
These wallets types will fall under 2 main categories:
Private Key Ownership
- Custodial — the wallet provider holds your private keys. These wallets are typically very easy to set-up and use (username/password), with the provider handling the technical details, for generating and securing the private keys. But although this does simplify set-up and use, it means the provider has control over your assets and if the wallet provider experiences a security breach or goes out of business, you could potentially lose access to your cryptocurrency
- Non-Custodial — also known as self-custody, are wallets where only you control the private key. This means that only you have access to your crypto assets and no one else. And with this great power comes great responsibility. You will need to understand how to safely secure and use your key. Unlike when you lose your password, there is no helpdesk to call to recover your access
Accessibility
- Hot — a wallet that is connected to the Internet. Think of this like a wallet you keep in your back pocket or purse. Easily accessible, but you wouldn’t put your life savings in it
- Cold — these wallets may also be commonly referred to hardware wallets. They are not connected to the internet and thus less accessible, because of this they are ideal for storing larger sums (less accessible to online threats, such as hackers)
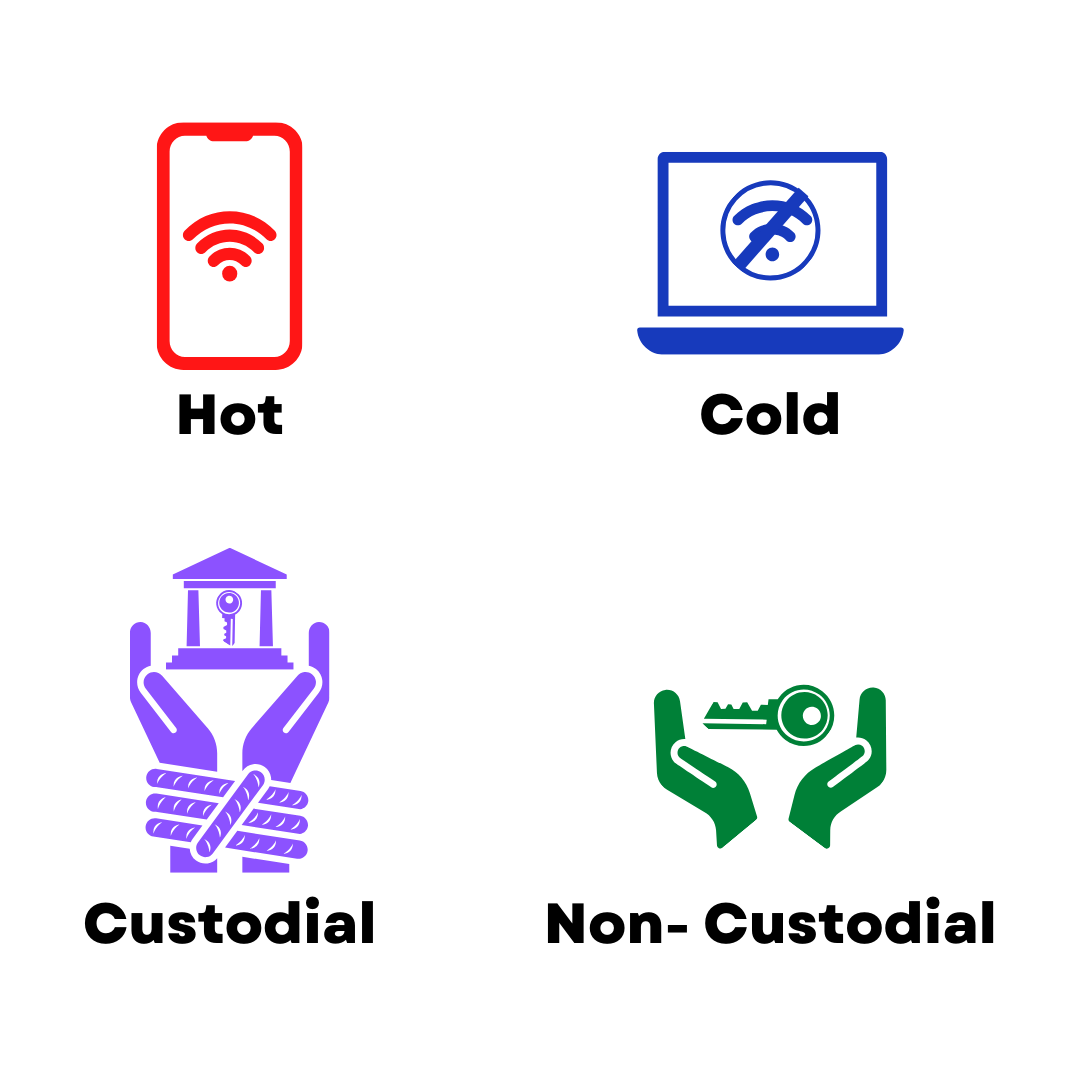
In articles to follow, we will take you deeper into understanding of wallet types, how they work, how to choose a wallet and most importantly, the best practices for how to securely manage and use your cryptocurrency.
Our mission is to help you gain a good understanding of what cryptocurrency is and feel confident in how to use it safely.
Stay tuned for more content from C4’s Cryptocurrency Essentials Committee!
This article was written by our CryptoCurrency Essentials (CCE) Committee.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Overview
Hardware wallets are dedicated, special purpose devices that generate and store cryptocurrency private keys. These devices are only used to securely generate cryptocurrency keys and to sign transactions, and offer no other functionality like a typical mobile phone or laptop computer. In contrast, a software wallet is any wallet that generates your keys on a typical computing device such as a phone. Hardware wallets have advantages over software wallets, particularly when it comes to security. Let’s discuss some pros and cons of hardware wallets.
Pros of Hardware Wallets
The key advantage of hardware wallet devices is security. These devices offer the highest level of security that most cryptocurrency consumers will interact with. The reason for this security is the fact that crypto keys are generated and stored entirely offline.
On a normal software wallet, the keys are generated and stored on a device such as a mobile phone or PC. These are general purpose computing devices that connect to the internet. This means there is a higher attack surface — more ways that hackers can try and steal your cryptocurrency! For example, malware that scans your device looking for seed phrases or wallet files. There are also attacks such as malicious wallet software — where an attacker tricks you into installing a fake wallet that steals your coins.
With a hardware wallet, however, your keys are generated on a device that doesn’t do anything else — it only generates cryptocurrency keys and signs your transactions. The seed phrase should only ever be backed up on paper or metal. If this step is followed, the only way an attacker could steal your coins is to physically steal a copy of your seed phrase. This is still possible, but much less likely than widespread malware attacks.
Another advantage is that interacting with the device gives a user more time to “think twice” before entering a seed phrase or signing a transaction. For example, you may find it odd that a malicious website is asking for your Ledger seed phrase when it should only ever be entered into the device itself. Or, the act of fetching your wallet from a home safe may give you time to think about sending coins off to a “doubling scam”.
A third advantage of these wallets is that the software/firmware is most often open source and well-audited by the engineering community. People regularly review the source code and even attempt to break into the devices to find security flaws. This community effort can help prevent security holes in hardware wallets.
Cons
However, there are some cons to hardware wallet use. The first is simply a barrier to entry. You must purchase a device to start using the wallet. In contrast, anyone with a phone or PC can download a software wallet to start using cryptocurrency. Devices can cost anywhere from around fifty dollars to hundreds of dollars, which can be costly for some users.
Users may also find that hardware wallets are less usable for day-to-day transactions, such as online purchases or paying for coffee. Sending from a hardware wallet requires the device itself, plus a PC or laptop the device can connect to. Mobile wallets, for example, are more streamlined for daily purchases.
Another con is that hardware wallets don’t necessarily prevent phishing or other social engineering attacks against users. You may still be tricked into entering a hardware wallet seed phrase into a phishing website, for example, or tricked into signing a malicious transaction with the device. The only help a hardware wallet offers in terms of phishing prevention is time to “stop and think” while you fetch the physical device and seed copy from a safe location.
Hardware wallets can theoretically be vulnerable to supply chain attacks, where a malicious seller can replace the firmware on the device. This firmware could use a predefined set of seed phrases that the attacker has copies of, for example, allowing them to steal your coins at a later date.
One final challenge of hardware is the importance of diligent backups of the seed phrase. The seed phrase must only be stored offline — on a medium such as paper or metal. Users must ensure multiple copies are available and protected from fire, flood, or theft. It is more involved backing up a hardware wallet seed than a software wallet seed that might be easy to store in an encrypted password manager or other secure cloud service.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

A recovery phrase (sometimes known as a seed phrase) is a series of words generated by your cryptocurrency wallet that gives you access to the crypto stored within that wallet. Think of a wallet as being similar to a password manager for crypto, and the recovery phrase as being your backup access point. As long as you have your recovery phrase, you’ll have access to all of the crypto associated with the wallet that generated the phrase — even if you delete or lose the private key.
One of the basic principles of cryptocurrency is the idea of “self-sovereignty”: you should be able to access your crypto without having to prove your identity, and you shouldn’t have to rely on a bank or other institution to store it safely.
How does a blockchain know which crypto is yours? It uses algorithmically generated password-like codes that only the holder has access to. When you first set up a crypto wallet — it generates a string of simple words, which is your recovery phrase (sometimes also known as a seed phrase). The wallet also uses the recovery phrase to algorithmically create private keys — which allow you to send or spend your crypto.
The reason recovery phrase is a series of 12 to 24 simple words (like “army,” “energy,” “fabric,” “lucky,” “opera,” “stereo,” “trash,” or “void”) rather than a numeric password is because long strings of numbers are difficult for humans to remember or even transcribe correctly — think of how hard it can be to input a long wifi password. Your recovery phrase unlocks your wallet, along with the private keys associated with all the crypto in the wallet.
Some important points to remember:
- Since only you know the recovery phrase, keeping track of it is of the utmost importance
- Anyone with your recovery phrase can gain access to your crypto.
- If you delete or lose your wallet’s private key without carefully saving your recovery phrase, you lose access to your crypto.
How Does a Recover (Seed) Phrase Work?
When you create a crypto wallet, a recovery phrase is automatically generated (in most wallets). The recovery phrase is a representation of a long string of random numbers — and your wallet uses it to generate the private keys that let you send and spend your crypto. The reason the recovery phrase is given to you in word form (rather than a long string of random numbers) is because humans are better at remembering and interacting with a series of words. But you shouldn’t rely on your memory for storing your recovery phrases. Each recovery phrase is pulled from a list of 2,048 simple words. The recovery phrase idea was widely adopted after 2013’s Bitcoin Improvement Proposal 39 (BIP-39), which established a standard for a “deterministic wallet” — which most wallets are now — in which one recovery phrase would control all of the private keys held in the wallet. The standard also makes major wallets intercompatible: if you want to switch wallets, you just need to enter your recovery phrase into the new wallet and your crypto will be available there. If you lose or delete a wallet, you can even recreate it using your recovery phrase alone. Keeping your recovery phrase safe from hackers, phishing attacks, or just simple loss is absolutely crucial.
How can you store a recovery phrase safely?
There’s a wide range of strategies about how to best secure recovery phrases, which tend to vary based on how much crypto you have and how much you value security vs. convenience.
One very powerful way to secure a recovery phrase would be to split it between safe deposit boxes in multiple locations (making sure there’s redundancy in case something were to happen to any of the locations). Obviously this is not very convenient.
Some people use specialized services to engrave recovery phrases into durable materials like stainless steel but, or many people, simply writing your recovery phrase down and keeping copies in more than one safe location is a solid approach.
Using the mobile version of Coinbase Wallet (which is separate from the main Coinbase app you use to buy or sell crypto) you can opt in to the encrypted Google Drive or iCloud recover-phrase backup feature, which stores an encrypted version of your recovery phrase in the cloud. You should also keep a copy of your recovery phrase somewhere safely offline.
The bottom line is: as long as you have your recovery phrase, you have your crypto. If you lose a hardware wallet on a bus or break a phone containing a software wallet, you haven’t lost your crypto — you can simply enter your recovery phrase into another wallet.
What happens if you lose your recovery phrase?
If you accidentally throw out the scrap of paper your recovery phrase is written on, forget which book you hid it in, or die without passing it on to an heir, you lose access to your crypto.
Remember: If you lose your recovery phrase, you lose access to your crypto.
If I’d prefer not to manage my recovery phrase, are there other options?
Sure. If you buy crypto via centralized exchange, you don’t actually have to immediately move it to a separate wallet (or ever, it’s up to you). Instead, you might choose to leave it in your exchange account, in which case the exchange automatically holds on to it via a “hosted wallet.”
What’s the difference between a recovery phrase and a private key?
Private keys allow you to send or spend some of your Bitcoin, Ethereum, or other crypto — they’re algorithmically derived from the long string of numbers represented by your seed phrase.
Your recovery phrase gives you access to your wallet and all the private keys in the wallet. You can think of a crypto wallet as being like a password manager for your crypto — as long as you have your master password (the recovery phrase) you have access to all the associated crypto.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Manan Vora and Tom Brandl.
Other CCE Committee articles:
Self Custody Wallet Pros and Cons
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

There are a lot of misconceptions regarding the differences between cryptocurrency keys, addresses, and wallets. To provide more clarity on this topic, let’s look at their characteristics one by one.
Keys
There are two types of keys: public keys and private keys. Public keys are comparable to account numbers. They can be freely shared with everyone, and anyone can potentially send transactions to them.
A private key is simply a number, picked at random. Ownership and control over the private key allows control over all funds associated with the corresponding bitcoin address. The private key is used to create signatures that are required to spend cryptocurrencies by proving ownership of funds used in a transaction and must remain secret at all times. Revealing it to third parties is equivalent to giving them control over the bitcoin secured by that key. The private key should also be backed up and protected from accidental loss, because if it’s lost all of the funds secured by it are forever lost, too. You should NEVER, under any circumstances, share your private key(s) with any other person. It’s best to store them in the most secure way possible (e.g. on a paper wallet or a hardware wallet).
Wallet Addresses
A wallet address is a randomly generated set of numbers and letters which represent a unique location on a blockchain similar to a bank account number at a bank. Here is an example of a wallet address: the first Bitcoin address ever: 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa. (Do not send funds to this address)
Wallet addresses can be created by anyone, for free, without needing a third party. You can create as many public addresses as you like or need. Wallet addresses are public and can be safely shared. Anyone with this address can send cryptocurrencies to the wallet associated with it. Think of an address as a bank account number.
Key Points to Remember:
- A private key is a string of random numbers that is generated using wallet software
- From the private key, we use a cryptographic function to generate the public key
- From the public key, we use a hash function to generate the address
- There can be multiple private keys, public keys, and addresses generated from the master private key
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Manan Vora and Tom Brandl.
Other CCE Committee articles:
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Private Keys and Key Backups: What’s the Difference?
Private key, seed phrase, wallet, blockchain address — crypto can be confusing! If you feel like you’re not sure which one’s which, then this is the article for you. Here, we get into the nitty-gritty of private keys and recovery phrases, their relationship and the differences between them.
Private Keys — Invisible Masters of Crypto
When all is said and done, private keys are the central element of cryptocurrency ownership. Blockchains are digital storage networks, and having the private key for a given address on a blockchain means that you control everything in that given address.
It’s important to note that there are also public keys in addition to private keys, which on the surface might seem confusing, but the difference is simple. Think of your public key as similar to your bank account number. Just like you share your account number with others so they can send you money, you can share your public key with others so they can send you cryptocurrency. However, unlike your bank account number, your public key is a long string of letters and numbers that is specific to the cryptocurrency network you’re using.
On the other hand, your private key is like your banking password. It’s a secret code that only you should know and use to access your cryptocurrency holdings. With your private key, you can access and manage your cryptocurrency, including sending it to others.
So where does the private key come from?
When you want to receive cryptocurrency, you need to create a blockchain address. This address is unique to you and serves as a digital mailbox for receiving cryptocurrency from others. However, in order to access the cryptocurrency that you receive, you also need a private key. This private key is generated when you create your blockchain address and serves as a secret code that only you should know.
It’s incredibly important to keep your private key safe and secure because it gives you control over your cryptocurrency. If someone else were to get hold of your private key, they could access and transfer your cryptocurrency without your permission. This is why it’s crucial to keep your private key secret and secure at all times.
However, private keys can be difficult to manage because they are typically long and complicated strings of alphanumeric characters. To make it easier for you to access your cryptocurrency, many wallets also generate a recovery phrase or backup. This is a series of words that can be used to recover your private key and gain access to your cryptocurrency holdings if your wallet is lost, stolen or damaged. It’s important to keep your recovery phrase safe and secure as well, as anyone who has access to it could potentially access your cryptocurrency holdings.
Recovery phrase (back-up): Your Crypto Fingerprint
The recovery phrase — sometimes called the seed phrase or mnemonic phrase — is a 12, 18, or 24-word pattern generated each time a new wallet is created. Unlike your private key, which relates to just one blockchain address, the recovery phrase is a derivative of your entire wallet, and all private keys stored there.
In layman’s terms, a recover phrase is the “master key” for all of your crypto accounts — it is your private keys in mnemonic form. These words, when entered into another crypto wallet (in the correct order) will recover all of the private keys you were storing on your original wallet. The purpose? Giving you control. Having this phrase means that even if you lose your private keys, you’ll still have access to your blockchain assets.
Let’s take the example of Bitcoin. A Bitcoin public address for example, might look something like this 13mMU4BJWkx6WYqN8gJZozYnRpML71HbgF (Do not attempt to send funds to this address). The public address has a corresponding private key associated with it, which would look like a 256 character version of this: KwdjuN2xEabumdg8eyGQhjFpFYjd4xSqpgnFo8yEKrcFNUPQ4JoM. A private key can be very long and confusing, and it can only access the funds associated with that specific address.
On the other hand, a private seed or mnemonic phrase is much more user-friendly. For example, a 12 word private seed or mnemonic phrase, also known as a BIP-39 phrase, could look like: “siren exit romance abuse bulb suffer ostrich budget verify museum spell accent”. This phrase is more human-readable and can be used to restore funds for multiple addresses and private keys associated with a wallet.
In other words, the private seed or mnemonic phrase can restore all of the private keys associated with a wallet, not just a single one. This is why it’s sometimes considered a master key, as it gives access to all of the crypto assets held in the wallet.
Key Points to Remember:
- A private key and a recovery phrase (backup) are two closely related concepts that are central to securing digital assets on a blockchain.
- Both provide a vector for accessing your blockchain assets, but do so in different ways and have different vulnerabilities.
- Private keys in raw form are 256 characters long, making them impractical for storing, securing and transacting with.
- Your recovery phrase is essential if you lose access to your wallet. Unlike a private key, the seed phrase is a 12, 18, or 24-word pattern generated each time a new wallet is created. Unlike your private key, which relates to just one blockchain address, the recovery phrase is a derivative of your entire wallet, and all private keys stored there.
- Recovery phrases and private keys are two halves of the same whole, but need to be managed differently.
Stay tuned for more additional information in upcoming articles from our CryptoCurrency Essentials Committee!
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Manan Vora and Tom Brandl.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Overview
Love crypto, but worry about its security? Cryptocurrency technologies are powerful because they allow you to hold your own keys for your money, rather than trusting a third party such as a bank. However, this opens up individual users to losses via scams and hacks that steal their crypto keys.
One very secure solution for individual key storage is a special device called a hardware wallet.
What makes these wallets so secure is that they generate these cryptocurrency keys entirely offline, and just for you. Rather than on a PC or mobile phone, that are more vulnerable to hackers, or with a 3rd party, such as an exchange. If you do not own your key, you do not own your money.
Hardware wallets, although great for security — are less ideal for day-to-day purchases. Which is why they are often used as savings accounts, versus ‘cash in your pocket’ functionality. These wallets are generally considered the most secure wallet for consumers, but care is required for proper use and storage of the keys. Here are some security pitfalls to be aware of.
Seed Phrase Management
The most important component of hardware wallet security is the management of the device’s seed phrase. A seed phrase is a collection of 12–24 words that serve as a critical backup of your wallet. This data grants access to all of the cryptocurrency balance stored in its wallet. So if you send 2 Ethereum and 1 Bitcoin to this wallet, the only way to restore access to the coins in the event your hardware wallet is lost or broken is to have a copy of the seed phrase.

The first important item in our hardware wallet security checklist is to retain multiple copies of the seed phrase, not just the wallet itself. Seed phrases should be written on paper or engraved in metal, and stored in safe locations. One example might be a home safe, a hidden location in the home, or another location protected from fire/flood/theft. Another offsite location should be chosen, such as a bank safety deposit box, or the home of a trusted family member or friend. Both of these offsite locations require some level of trust — but offsite backups are critical in the event the original is destroyed. A bank safety deposit box may be seized, so a user may consider additional protection like a friend’s home or the addition of a BIP39 passphrase. The use of a BIP39 passphrase, stored in a separate location from the seed, can provide an additional layer of protection if the seed is compromised.
The second item in our checklist is the form of the seed phrase backup. Yes, how you backup your seed phrase is very important to your security. A hardware wallet seed should only be copied into a physical form such as paper or metal, never stored in a PC or mobile phone. If you use a hardware wallet, you should never store a copy of the seed in a picture, document, or even encrypted form such as a password manager. Why?
The entire purpose of a hardware wallet is to generate and store keys offline, on a device that doesn’t have access to the internet. A mobile phone or PC is connected to the internet, and offers general-purpose computing functionality. This offers a higher attack surface — more opportunities for hackers and thieves to gain access to your seed data and steal your cryptocurrency. By storing an offline wallet seed phrase on a general-purpose device like a PC, you break the security model of this offline wallet. So only backup your hardware wallet phrase in physical form!
Device Purchases and Management
Another noteworthy security practice for hardware wallets is how you purchase the wallet. These wallets run open-source software scrutinized by the cryptography and security community. But how can you know that the wallet is loaded with the same open-source software and not a malicious version?
The simplest way to protect against supply-chain attacks is to purchase these devices directly from the manufacturer (for example, Trezor). Do not purchase hardware wallets from third-party sellers such as Amazon or other online stores.
Phishing Awareness
Even though hardware wallets (with offline backups) are very secure, users are often tricked into giving up access to their coins via social engineering. For example, after the Ledger purchase database was compromised, users were targeted with various phishing scams. In one case, users were sent a fraudulent but legitimate-looking email asking them to “update their Ledger”. This led to a website that installs malicious software on their PC. Other similar campaigns prompt users to enter their 12–24 word seed phrases, giving the scammers full access to their wallets.
Never enter your seed phrase into any online form, even one that looks like it came from the manufacturer. Never install software on your device if requested by email, Twitter, etc. Never believe anyone claiming to be a support agent for a wallet. The only place you should read for software updates and support should be the manufacturer’s official website and support channels. Take your time when you need help — scammers want you to act quickly so they can trick you into giving up your coins.
Hardware Wallet Stories
Let’s suppose Alice has purchased 1 Ethereum and 0.5 Bitcoin she wishes to self-custody. Alice is primarily concerned with malware threats as she uses her PC for web browsing, and wants to keep her cryptocurrency wallets separate from her day-to-day devices. Alice purchases a Ledger device directly from the manufacturer, generates her seed, and writes it down on laminated paper. She stores one copy in a quality home safe, and another at her parent’s house. When she decides to sell half of her Ethereum, she connects her Ledger device to her PC to sign the transaction.
Bob is a well-known businessperson in his town and loves to share his passion for cryptocurrency. Bob doesn’t ever talk about his exact holdings, but it is known that he uses Bitcoin and has a fairly high net worth from his successful car business. Bob worries his home may be targeted for theft. Bob purchases a KeepKey device and sets up his seed phrase. In addition to the seed, Bob generates a strong, random BIP39 “diceware” passphrase (rolling dice to pick words from a list). Bob sends 10 Ethereum and 5 Bitcoin to this main wallet. Bob stores the seed phrase on an engraved steel plate in a hidden location in his home, rather than his document safe in the bedroom. Bob also stores a paper copy of the seed in a bank safety deposit box that is kept secure at all times. The BIP39 passphrase is stored in his encrypted password manager, while his seed is only stored in physical form.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Other CCE Committee articles:
What is a Cryptocurrency Wallet?
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

How Can Organizations Prove They Have the Crypto They Claim to Have?
The CryptoCurrency Security Standard (CCSS) is a free and open set of industry guidelines and best practices for securing cryptocurrency and related systems. The CCSS recommends that organizations implement a variety of security controls to protect their cryptocurrency holdings, such as creating cryptographic keys and seeds on a system with sufficient entropy, using secure communication channels, and conducting regular security audits. However, these security controls only take us so far and proof that the assets an organization claims to hold remains vital. This is why systems that control assets must prove that they are solvent in order to be CCSS certified.
What is Proof of Reserve (PoR)?
Proof of Reserve (PoR) is a method that an organization can use to prove that it has the funds or assets that it claims to have. PoR is important in the context of cryptocurrency exchanges and other organizations that hold cryptocurrency on behalf of customers. In these cases, PoR can help to provide assurance to customers that their cryptocurrency is safe and that the organization has the assets it claims to have.
There have been instances where exchanges or other organizations have failed to maintain sufficient reserves of cryptocurrency, leading to financial losses for customers. A recent example of this is the FTX meltdown, wherein more than $8 billion dollars worth of customer funds have been lost, and FTX could owe money to more than one million people and businesses. FTX lent its affiliate, Alameda Research, billions of dollars which led to FTX’s customers being unable to access their assets. The bottom line is that real people with bills, mortgages, and families, who thought their assets were being safely held, have been deeply impacted by the loss of their funds.
Why do we need CryptoCurrency Security Standard’s PoR Control?
The CCSS PoR control means that the organization holding customer funds either publishes enough information to prove, for example, 1:1 bitcoin backing, or one can view on the blockchain itself to see if they are operating a fully solvent system or an insolvent system.
The CCSS and PoR can provide assurance that customer deposits are safe and that the institution has the funds available to meet its obligations. This can be especially important in cases where an institution is not federally insured, there is concern about the financial stability of the institution, or customers are requesting proof of assets.
CCSS audits are conducted by an external third-party auditor and a peer reviewer. As with all standards, no controls are perfect silver bullets. But it is better to have something than nothing. The CCSS certification requires a PoR audit, completed and published online, that proves full control of all funds held by the information system. The PoR audit must be signed by an independent party that attests to the accuracy of the audit at the time it was performed. Therefore if FTX had undergone a CCSS audit the lack of funds would have been identified and customers would have known by the lack of certification that something was amiss. If we as an industry demand that we won’t use custodians that aren’t CCSS certified, then people will be able to make more educated decisions and lower the risk of losing their assets.
As of the date of this publication, the only system that has completed a CCSS audit and been certified by C4 is Fireblocks Limited, however there are additional systems being audited. You can keep an eye on the growing list of security conscious CCSS certified organizations on our website.
PoR helps to build trust and confidence in financial institutions and other organizations, and it helps to ensure the stability and integrity of the financial system as a whole. Knowing that a standard, created by cybersecurity and cryptocurrency experts, exists and is open to use, we must ask ourselves: why might custodians holding others’ money NOT want to prove solvency? If the reserves are as promised, why would a company not want to provide that assurance to customers?
You can find more information about PoR in this blog post written by CCSS Auditor Marc Krisjanous.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.
What is the CryptoCurrency Security Standard?
The CryptoCurrency Security Standard is an open, free standard (created by industry experts) for securing cryptocurrency systems.
CCSS audited systems will either be identified as Self Custody, Qualified Service Provider (QSP) or a Full System (FS). You can read more about these designations in this blog post.
Any entity whose systems have been audited and certified will be listed on our website and can be seen at https://cryptoconsortium.org/completed-ccss-audits/. Don’t trust, verify. Any entity who claims to be certified but is not listed on our website does not, in fact, have a current, valid, CCSS certification. Certifications are point in time and are valid for one year from the certification date.
Fireblocks Limited has the first system ever to be CCSS certified!
Fireblocks Limited is the first company with a system to ever receive a CryptoCurrency Security Standard (CCSS) Certificate of Compliance, after having been audited by a third-party CCSS Auditor. Fireblock’s system, comprised of Fireblocks Hot and Cold Vaults, Fireblocks Secure Transfer, and Fireblocks Authorization Workflow, received a Level 3 Qualified Service Provider (QSP) Rating. Completion of this audit confirms that, at the point in time of the audit, the processes that Fireblocks’ system uses to create, store, and manage keys is secure and that they’ve maintained processes and practices that met the required levels of oversight, security, and monitoring in order to protect their system.
It is important to note, however, this does not verify that another system which uses Fireblocks is CCSS certified at any level. Any third party who uses Fireblocks’ system must be audited for compliance in the areas where Fireblocks does not have control and certified (or not) in an audit for their cryptocurrency system.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

C4’s CryptoCurrency Security Standard (CCSS) is the only standard that certifies for securing cryptocurrency systems.
CCSS is a set of requirements for all information systems that make use of cryptocurrencies, including exchanges, web applications, and cryptocurrency storage solutions. By standardizing the techniques and methodologies used by systems around the globe, CCSS ensures a balance between security and usability so that end-users can easily make educated decisions about which companies and products they wish to align.
CCSS audited systems are identified as Self Custody, Qualified Service Provider (QSP,) or Full System (FS).
Self Custody
A CCSS Self Custody system controls all keys to the system that controls the entity’s own funds. Self Custody systems do not have control over customer funds.
If an entity is using a service provider as part of their cryptocurrency system, it could impact the security of systems that provide cryptocurrency functions, therefore the entity will need to be certified for a Full System certification instead of the Self Custody certification.
As an example, if a system uses a third-party wallet provider in which the third-party participates in the key management, the system would no longer be Self Custody.
Qualified Service Provider
A CCSS Qualified Service Provider (QSP) is a system that meets many of the requirements for CCSS certification with the exception of the few requirements that another system has control over. A QSP is a system that facilitates a subset of custody services to other systems and therefore is only required to meet certain requirements. This means that if a system uses a QSP, the audit focus is only on the few remaining requirements to become certified.
An example of a QSP is a system that participates in signing a customer’s transaction by being in control of one or more of the signing keys used to sign said transaction. The customer controls the other key/s.
When customers are responsible for the other keys, the assessed entity’s system has no ability to control how they are secured at rest or when they are being used since they are within the customer’s environment. Because of this, the assessed entity’s system cannot meet the requirements for controlling the signing keys in totality since some of the signing keys are outside of their control.
Full System
A CCSS Full System is a system that meets all applicable CCSS requirements in totality.
A system that provides evidence to the CCSSA that it controls all signing keys will be audited as a CCSS Full System. Full Systems have control over customer funds.
Conclusion
If a system doesn’t meet all the requirements, then that system is either a QSP or uncertified. If a system has control of only some keys and does not meet all the requirements then it’s not a full system (and can’t be certified as a Full System), it’s a QSP. If a system controls all keys and does not meet all the requirements, it’s uncertified. If a system controls all keys to the system that controls the entity’s own funds it is Self Custody.
Don’t trust. Verify.
*Key management is a complex concept in which there are many nuances. This article provides general guidelines, however, each assessed system will require individual scrutiny by a CCSSA.
More articles about the CCSS, written by CCSSA Marc Krisjanous, can be found here: https://www.linkedin.com/in/marckrisjanous/recent-activity/posts/
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

The CryptoCurrency Security Standard, or CCSS, is a range of requirements curated by C4’s CCSS Steering Committee for all information systems that make use of cryptocurrencies, including exchanges, web applications, and cryptocurrency storage solutions. By standardizing the techniques and methodologies used by systems around the globe, end-users will be able to easily make educated decisions about which products and services to use and with which companies they wish to align.
The CCSS is designed to complement existing information security standards, by introducing guidance for security best practices with respect to cryptocurrencies such as Bitcoin.
The CCSS is not intended to replace these standards; in fact, following the CCSS to the letter while ignoring standards like ISO 27001:2013 will likely lead to compromise. The CCSS is a cryptocurrency standard that augments standard information security practices. As with any standard, knowledgeable and competent security professionals and/or auditors are vital when implementing any information system to protect against types of attack as well as the appropriate handling of all potential risks.
The standard is maintained by the CCSS Steering Committee. Current committee members are S. Dirk Anderson, Andreas M. Antonopoulos, Petri Basson (committee chair), Noah Buxton, Jameson Lopp, Joshua McDougall, Michael Perklin, and Ron Stoner.
The CCSS steering committee’s goal is to ensure the standard remains up-to-date with industry best practices and remains neutral.
Head over to cryptoconsortium.org to learn more about C4’s CryptoCurrency Security Standard!
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

You probably use cryptography multiple times a day. It is used frequently, from websites to your smartphone, and serves an important function. And if you use Bitcoin and other cryptocurrencies, cryptography serves a critical security function. Cryptography is the art of secret writing, and cryptographic functions enable you to securely send bitcoin, ether, and other cryptocurrencies.
Let’s discuss the difference between symmetric and asymmetric key cryptography. Symmetric key cryptography uses one key for both encryption and decryption. Asymmetric key cryptography, also known as public key cryptography, uses two keys, one for each operation. Think about it as a lock on your front door. If you can both lock and unlock your door using the same house key, that is akin to symmetrical cryptography. If you needed to use one key to lock the door and another key to unlock the door, that would be comparable to asymmetric cryptography.
In asymmetric cryptography, two different keys are used, the public key and the private key. As is probably obvious from the name, the public key can be ‘public,’ and can be shared freely.
Going back to the front door example, if the key to your front door was made public but only allowed for the locking of the door, you wouldn’t need to concern yourself with theft; the key that unlocked the door could be kept private. This is similar to how asymmetric key cryptography works. The public key can be shared without being a security risk because that key doesn’t open the door.
In Bitcoin, your private key must be kept secret because it effectively unlocks the door to access your bitcoin.
One crucial part of public-private key pairs is that the public key can be derived from the private key. This means that if you know the private key you are able to figure out the public key. However, the reverse is not true; the private key cannot be derived from the public key. If you have a public key but no private key, you’d be unable to access the private information.
Let’s compare this to the front door example. You could use the (private) key that unlocks your front door to retrieve the (public) key that locks the door. So basically, the private key can lock and then unlock the front door. On the other hand, the public key can lock the front door, but there is no way to use this public key to unlock the door.
With bitcoin, this matters because it means anyone can have access to your public key, which is perfectly okay. The public key is used to find the bitcoin address where bitcoin is sent. But remember, knowing a public key and bitcoin address doesn’t allow access to received bitcoin. This would be like the public house key having the home address written on it, and it not being a security risk because this information won’t unlock the front door. Taking this analogy a step further, having a home address allows mail to be delivered through a slot in the front door, in the same way, having a bitcoin address allows bitcoin to be received. And just as the mail, once put through the mail drop, can no longer be accessed, once bitcoin has been received, the public key can’t access it.
Take a look at cryptoconsortium.org for a more detailed outline of the content you need to understand to become a CBP, and check out our YouTube channel to learn more about Bitcoin. For an in-depth look at how Bitcoin works, enroll in C4’s prep course and/or read our CBP prep book. Good luck, future CBPs!
Note: This front door private-public key example is an imperfect analogy, however it does provide a relatable comparison to help understand the basics of how asymmetric cryptography works.
This article was written by our CryptoCurrency Essentials (CCE) Committee.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

C4 is excited to announce the addition of the Certified Bitcoin Professional Prep Course to the Thinkific platform. While the course is still available on Udemy, Thinkific’s platform allows C4’s offerings to expand and provide additional learning and certification opportunities to a broader audience. Innovative colleges and cutting-edge companies have already jumped at the chance to have their students and employees educated and certified through C4. Increasingly, businesses are seeing the need for Bitcoin knowledge and certifications as cryptocurrencies continue to change how our world works. Using Thinkific’s platform creates the opportunity for C4 to customize packages and bundles for institutions and companies wanting to be at the forefront of this new space.
The CBP course is a great way to study for the CBP exam if you are a visual or auditory learner and want a step-by-step explanation of the material needed to succeed on the exam. Experts guide you through the material and there are short quizzes and assignments to check your understanding. You also have the chance to ask questions and receive answers from C4. The course content is based on the CBP exam, and those who take the course are well prepared and ready to become CBPs! Both course platforms enable updates to the material so you can be sure that any new material added to the exam will also be added to the course when you are ready to renew your certificate (certifications are valid for 2 years).
In the CBP prep course you’ll watch videos and follow the course with supplemental materials to help you prepare for the exam. Prefer an ebook because you learn better by reading? You can access that on our website. You can even purchase both resources to help you prepare!
C4 has several projects in the works to assist the crypto community, both those new to the space and experienced professionals, and we can not wait to share them. A Certified Ethereum Professional (CEP) exam prep book is in the works, and a CEP exam prep course and many others will be added in the future as C4 continues to create educational material and certifications for the ever-expanding world of cryptocurrencies. Feel free to comment below on topics you’d like to see us cover and come Learn More with C4 by taking our CBP prep course!
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Cryptocurrency and blockchain technology have impacted almost every industry, and as it continues to become more known and used, opportunities are rising! Better yet, you don’t need to have programming skills! Which begs the question, what kind of careers are available for the non-technical crypto enthusiast? Here are 5 ideas that might help you find your dream job.
Marketing
Not a techie? It’s all good because crypto companies need help spreading the word! Creating marketing content can be one of the critical aspects of connecting buyers and sellers in the fast-paced world of blockchain technology. Learning about the non-technical aspects of crypto is essential for people who want to work in blockchain and crypto adjacent roles.
Graphic Design and Art
The explosion of blockchain technology has led to an exciting opportunity for artists to sell their work as NFTs (non-fungible tokens) online, but there is more to the industry than just that. Blockchain companies and those that use cryptocurrencies also need artists and graphic designers to help educate others on their products, mission, and values. It’s common these days for artwork to be interspersed with just about all educational and informative materials out there. So, if you’re a fan of blockchain technology and love to create and design, there is certainly a place for you.
Writing
Companies that use cryptocurrencies need technical and non-technical writers. Non-technical writers are needed to explain how products work to investors without getting into the nitty-gritty. Developing a business plan or explaining what the investors will gain, takes not only the skills of a good writer, but also a knowledge of crypto. It takes skills to explain a complex topic in an easy-to-understand way. A well-developed understanding of crypto is essential, and our course and certifications will give you a leg up in this industry.
Project Management
All industries need managers to guide projects from inception to completion, and the blockchain industry and other industries that use cryptocurrency and blockchain are no different. If you enjoy playing a key role in actionable projects and working with others, then a project management job that requires an understanding of cryptocurrency basics might be a good fit for you!
Finance
As cryptocurrency exchanges and EFTs become more mainstream, many people will want to hire an expert to deal in the crypto market for them! Asset managers, traders, brokers, and analysts will require crypto knowledge and certifications.
Endless Possibilities — Off and On Chain
The list above consists of general ideas for makinge a move into blockchain technology, but there are so many more options out there!
For example, Certified Court Interpreter Elda Ellis of Translating Worlds has worked in the legal system for over a decade. She is also a Certified Bitcoin Professional. Elda is an educator who specializes in courtroom protocol, Bitcoin technology, and cryptocurrency. She has carved out her niche as an educator, speaker, and consultant for court reporters and professionals and has translated educational materials and books about cryptocurrency from English to Spanish. Elda says that “Bitcoin is also for language professionals. It’s an amazing technology & it’s here to stay. I have to share with my Interpreter & Translator colleagues this wealth of information because cryptocurrencies will touch every aspect of our professional life. It’s imperative we learn its nascent terminology.”
Another example is Joshua McDougall, a C4 board member (CBP and CEP) who recently left his career as a digital investigator and has started building blockchain-based games full-time. Joshua started SlowNinja in 2014 with the creation of the game Coindroids, and is currently working with a small team and community input to develop a new game in the Cosmos ecosystem. He says, “I’ve been obsessed with exploring how blockchains can improve a gaming experience for over seven years. In my previous role, my focus was keeping digital assets safe. Being able to use that experience, while combining my passion for this innovative technology with my love of games, is something I can’t pass up.”
Resources
Resources for those looking to branch away from the traditional 9–5 to explore independent opportunities are becoming increasingly available. Take for example Opolis, which is geared towards those who identify as freelancers, independent contractors, and digital nomads. Opolis is an Employment Cooperative offering employment benefits and shared services. Their goal is to “simplify your life and streamline business complexities.” It seems like a perfect match for crypto enthusiasts ready to branch out!
There are Certified Bitcoin Professionals worldwide who have carved out jobs for themselves as they’ve explored the intersection of blockchain technology and their own interests and skills. There are thousands of people who have made the move into blockchain technology and cryptocurrencies, and as the space continues to grow, there continues to be a need for more and more Certified Bitcoin Professionals and Certified Ethereum Professionals.
As you move forward in your crypto career, C4 provides the learning and certifications you need. More information about our study materials and certifications is available on our website: https://cryptoconsortium.org/certifications/
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Florida International University’s (FIU) Chapman Graduate School of Business now collaborates with the Cryptocurrency Certification Consortium (known as C4) to bring the Certified Bitcoin Professional (CBP) designation to FIU’s online Master of Science in Finance degree program.
Students in FIU’s master’s level Financial Innovation course are taught by Florent Rouxelin, Assistant Professor of Finance, about Bitcoin and open blockchains, in part using C4’s CBP exam prep book. Students sit for the CBP exam during the semester and leave the course as Certified Bitcoin Professionals, with the proof to show prospective employers that they understand this new, revolutionary technology.
Though some folks are still skeptical of cryptocurrency and blockchain technology, Bitcoin’s impact on international markets is undeniable. Bitcoin’s total Market Capitalization surpassed $1 trillion in February 2021. In October 2021, BITO — the ProShares Bitcoin Strategy ETF that tracks bitcoin price predictions — amassed $1.1 billion under management after just two days of trading. As a growing currency constantly expanding its usage and value, bitcoin has captured the attention of Fortune 500 Companies and countries all over the world. JP Morgan, Apple, PayPal, and Amazon all recently posted job listings looking for professionals versed in Bitcoin and cryptocurrencies.
For those unfamiliar, bitcoin is a form of digital money where transactions are recorded in a hash-linked data structure called a blockchain, which is secured through a game-theoretical consensus mechanism called proof-of-work. In essence, bitcoin is a peer-to-peer, borderless, open, public, and censorship-resistant digital currency that lives on the Bitcoin blockchain. Bitcoin with an upper-case ‘B’ refers to the network, and bitcoin with a lower-case ‘b’ refers to the currency.
Over 70 million blockchain wallets — the digital wallets used to store bitcoin and other cryptocurrencies — are currently in use. However, many of those wallets belong to people with very little knowledge of how to use or invest cryptocurrency (or cryptocurrency in general).
To keep up with this emerging market, educational resources, courses, and certifications are needed to validate people’s claims that they are professionals who understand the complex world of cryptocurrency.
The CryptoCurrency Certification Consortium (C4) is a nonprofit dedicated to establishing cryptocurrency standards. C4 provides this confirmation through the Certified Bitcoin Professional (CBP) and Certified Ethereum Professional (CEP) exams. Companies and hiring managers can feel reassured that those certified by C4 possess the knowledge necessary to work with cryptocurrencies. By being one of the first schools to work together with C4 to acknowledge the power and huge growth of cryptocurrencies in the world market, FIU’s Chapman Graduate School of Business will cultivate the leaders of the new era in finance being ushered in by open blockchain technology.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Curious about the benefits of Bitcoin’s open blockchain? Read on!
The word “Bitcoin” is being used by more than just those in the cryptocurrency industry. Bitcoin is in the news, all over social media, and becoming increasingly popular in the financial world, even recently being added as an ETF, or exchange-traded fund.
If you’re curious about Bitcoin, read on to learn some of Bitcoin’s benefits.
Resists Censorship
One of the greatest benefits of Bitcoin, is the Bitcoin blockchain can’t be censored. Bitcoin’s blockchain is a ledger of every Bitcoin transaction. The data isn’t stored on central server, but rather over a network of computers. This makes it incredibly difficult to hack, modify, or censor.
Peer-to-Peer
There is no centralized point of control, meaning each transaction is distributed between nodes that are equal, or peers. The fees incurred when sending bitcoin (lower-case “b” when referring to the currency) don’t go to a central bank. Instead, fees are rewarded to miners who are doing the work behind-the-scenes.
Open
Bitcoin is open to the public. Anyone, anywhere with an internet connection can use the Bitcoin blockchain.
Neutral
Another benefit of Bitcoin is that it’s neutral. The Bitcoin network doesn’t care who the sender or recipient is. The Bitcoin network’s focus is on transferring value. It turns hierarchy upside-down because it isn’t asking permission. We live in a permission financial society, where we expect to be given permission for how we can send or receive money (unless using cash) and this is a large part of why there are many skeptics.
Public
Did you know anyone can participate in the Bitcoin network? You can even run your own validator node as a participant. Why do this? The network of nodes establishes security, safety, and transparency, and you can be a part of it!
Bitcoin is also open to all to participate! Some banks won’t allow you to open an account without paperwork, permissions, and a certain investment. Bitcoin welcomes all.
Borderless
There are no borders with Bitcoin You can make bitcoin transactions with anyone, anywhere! Like the internet, Bitcoin is everywhere.

Want to learn more about Bitcoin?
We offer courses, certifications, and tons of educational knowledge. Get started now with this link: https://cryptoconsortium.org/certifications/cbp/
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.
What Is a Cryptocurrency Wallet? And What Kind Should You Get?

If you want to begin holding cryptocurrency, one of the first things that you will need to do is set up a wallet. But what is a wallet? Do you want a hot or cold wallet? And how do you safely download and/or purchase a crypto wallet?
When you think of a wallet, you may think of the envelope-like material you keep in your pocket or purse to hold your money. While a crypto wallet can keep your money safe, it does not contain a physical currency you can touch. However, it does allow you to access your crypto using your private key.
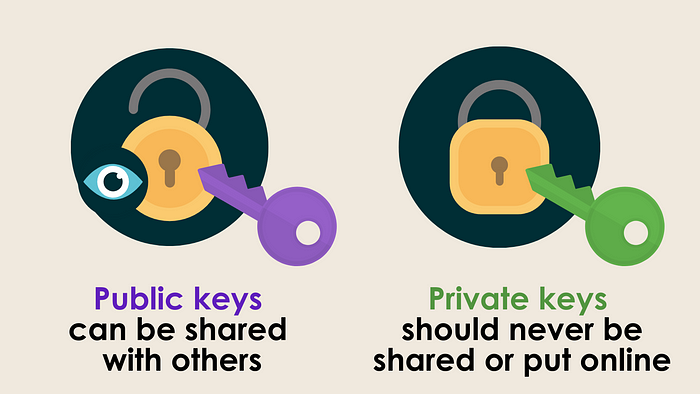
Public keys can be shared with others. Private keys should never be shared or put online.
You might be asking yourself, what are keys? First, it is essential to know that there are private and public keys. Your public key is like a bank account number in that it can be shared with others, money can be deposited to it, and can only be removed through authorization. (This is a simplification; if you want to learn more, check out C4’s study materials ) Private keys can be compared to your bank password that gives you access to authorize withdrawals. Your private keys provide you with access to your cryptocurrency and should never be shared with others or put online. In other words, the private key is to be seen only by the person who owns the address to keep your currency safe.
Because cryptocurrency is digital, your crypto isn’t physically in your wallet. Instead, using your private key gives you access to send and receive your crypto.
There are different wallets, and the type of wallet/s you use to hold your crypto will vary depending on your needs. Simply put, a wallet can be hot or cold.

Hot wallets are connected to the internet.
A hot wallet is connected to the internet. They are usually run by a third party, and your keys are kept in their database. This makes storing and accessing keys very easy. Log in to the database, and you can send your crypto in moments. However, hot wallets come with some risks. Because hot wallets connect to the internet, your crypto is vulnerable to hackers. Therefore, it is recommended that you do not leave more money in your hot wallet than you would have in a physical wallet.

Cold wallets are never connected to the internet.
On the other hand, a cold wallet, also known as a hardware wallet, is not connected to the internet and is used to store your keys and addresses offline. One of the advantages of cold storage is that you don’t need to worry about your private keys being stolen online. You should keep your cold storage in a safe location. The most significant risk to a cold wallet is your own forgetfulness.
Whether you choose a hot or a cold wallet, you will need to keep a backup to your wallet, a list of words called a seed. Write these words down multiple times and keep them in secure locations. These words will protect you, so you don’t lose access to your cryptocurrency.
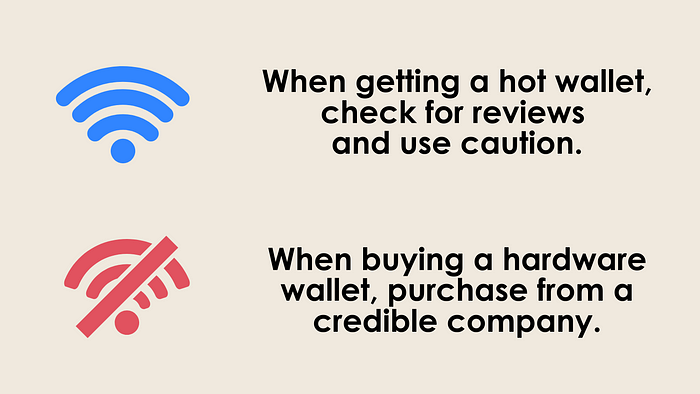
When getting a hot wallet, check for reviews and use caution. When buying a hardware wallet, purchase from a credible company.
No matter which wallet or wallets you use, you should always ensure that you safely acquire them. If you are downloading a hot wallet to your phone, make sure you check reviews, number of downloads, and be careful. If you’re purchasing a cold wallet, make sure you buy from a credible company’s website and check your package for tampering.
Ask a trusted friend for help if you need more information about which wallet might work best for you, but remember never to share your private keys! If you don’t have a trusted person who can help you with what wallet might be right for you, the below links may be helpful.
Stay safe out there, friends!
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Gas in Ethereum: It’s Not What It Used To Be!
The EIP-1559 Update
Before we get into EIP-1559, it’s important to know that EIP stands for Ethereum Improvement Proposal. EIPs are standards proposed by the Ethereum community to make changes to the Ethereum blockchain protocol. The recent and much-anticipated EIP-1559, which was included in the London hard fork, was first proposed by Ethereum creator Vitalik Buterin as a way to change how transactions are processed on the Ethereum blockchain and how new Ether is minted.
An Ethereum transaction occurs when an externally-owned account cryptographically signs an instruction and the state of the Ethereum Virtual Machine changes. To be added to the Ethereum blockchain, every transaction has a cost, known as gas, that must be paid in Ether to the miners.
With the EIP-1559 upgrade, Ethereum fees are now divided into base fees and tips, and used fees are burned to reduce inflation. Let’s break that down a bit.
Base fees, which are paid in Ether, now fluctuate depending on how congested the network is. And rather than a miner being given this base fee, the fee is burned. This upgrade aims to stabilize transaction fees by having the base fee increase or decrease by up to 12.5%. And the burning of this base-fee, rather than all going to a miner, reduces the supply of Ether that is circulating and thus makes it more scarce.
Tips are used to incentivize miners to prioritize transactions. During high periods of demand, users can decide to allocate ether, as a tip, to incentivize miners to add their transaction more quickly. During lower periods of demand, users are able to include a smaller amount of ether as a tip, or none at all, and won’t need to wait as long for it to be added to a block.
This change to the Ethereum protocol makes fees more predictable, reduces uncertainty in transactions for users, and limits the supply of Ether without creating a supply cap.
C4’s Certified Ethereum Professional (CEP) committee has updated the CEP exam based on the EIP-1559 (London) update.
If you want to read the proposal you can find it here: https://eips.ethereum.org/EIPS/eip-1559
More information can be found here:
If you are interested in analytics on the Ethereum fees and burn rate:
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

CBP Is Not Just For Men
Gone are the days when Bitcoin solely belonged to the sphere of long-haired technophiles. Lambos, steak, and “moon” now characterize Bitcoin’s culture and Bitcoin’s rainbow charts seem to be making more headlines than the Bitcoin whitepaper. However, this doesn’t mean that we should forget about Bitcoin’s origins and the fact that this technology emerged in part as a response to the 2008 financial crisis.
Bitcoin is revolutionary because it allows anyone to participate in finance by removing gatekeepers. This means that no matter your race, religion, gender, sexual orientation, location, and even credit score, if you have an internet connection you can participate in Bitcoin.
As a woman, accessibility to Bitcoin is a vision that I consciously strive to promote in this industry. It is also the reason why I decided to get my Certified Bitcoin Professional (CBP) designation. Having the CBP makes me feel more confident about my professional skills in an industry that too often gets infiltrated by ICO scammers, rent seekers and “get-rich-quick” swindlers. The certification also helps put my mind at ease knowing that I can succeed in an industry that is heavily dominated by men since my professional skills and experiences can get the recognition they deserve.
You may be wondering if the CBP is right for you, especially if you’re coming from a non-technical background like mine. There is no denying that Bitcoin is technically complex, but this exam isn’t overly technical. There are some excellent free resources available that can help you pass the CBP. “Mastering Bitcoin” — written by C4’s own board member and Bitcoin and open blockchain educator, Andreas M. Antonopoulos — is the book that I used to prepare for the exam. The free PDF version can be found here: https://github.com/bitcoinbook/bitcoinbook. I highly recommend using this text because the technical content is presented in a very clear and straightforward way. This text also works great for non-coders. I skimmed through the coding portion, which I highly recommend doing since it helps you learn a lot about Bitcoin’s internal workings, but it isn’t necessary to becoming a CBP.
If you’re more of an audio and visual learner, C4 offers a course that teaches you the fundamentals of Bitcoin and everything else you need to prepare you for the exam.You can find the course on Thinkific here: https://cryptoconsortium.thinkific.com/courses/CBP-course. Since I was already familiar with Bitcoin’s essentials, I didn’t take the course, but it is a great place for Bitcoin newbies to start.
As I already mentioned, I was worried that my lack of technical knowledge would somehow prevent me from doing well on the exam, but, to my pleasant surprise, the exam is crafted in a way that makes it accessible to everyone (thank you C4!).
For example, many of the exam questions focused on broad concepts that were discussed extensively in the book. To pass the exam, I had 20 minutes to answer 75 questions and I had to get 70% of the exam questions right.
Overall, I’d say that the exam turned out to be fair game. While I could not get through all 75 questions, I still passed and was able to prove my knowledge and understanding of Bitcoin. Of course, the best part about this whole experience is that after you pass the exam, you get a personalized certificate mailed to you. Having the proof that demonstrates I know my Bitcoin stuff feels really good ☺
The CBP is not just for men and I am living proof. I am now proud to call myself a Certified Bitcoin Professional and I’m excited at the opportunities that the CBP will bring not only to me, but to everyone seeking to make a meaningful contribution to this ecosystem.
- Ann Brody is a researcher who studies blockchain communities and decentralization. You can find her on Twitter here: @annbrody7
- This content is written by a volunteer who does what they want outside of helping C4. They don’t speak for our org, but we do appreciate their willingness to help out.
Written by: Ann Brody, CBP
Note from C4: The CBP Prep Course & Prep Book can be found on our website.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.

Earn your Certified Ethereum Professional Designation Today!
We’re excited to announce the launch of our Certified Ethereum Professional (CEP) exam! Thanks to the hard work of our CEP committee and the generous Gitcoin Grants contributions that pushed this forward, the CEP exam is now available for you to take on our website.
About the Certified Ethereum Professional Designation
A Certified Ethereum Professional (CEP) is knowledgeable about the Ethereum blockchain, Ethereum transactions, and the basics of Solidity programming language and how to use it to understand smart contracts on the Ethereum network.
CEPs have professional working knowledge in 33 topics which cover six (6) domains of Ethereum knowledge. These six domains make up the Common Body of Knowledge that all Ethereum professionals must possess to earn the CEP designation.
The following careers could benefit from certification:
- Accountants & Controllers
- Application Architects
- Call Centre Representatives
- Cryptocurrency Enthusiasts
- Developers & Software Engineers
- Entrepreneurs
- IT Professionals
- Professors, Teachers, and Educators
- Project Managers
- Sales & Marketing professionals
- Anyone Using Ethereum in Their Daily Lives!
The CEP Exam
The exam includes 75 multiple-choice and true/false questions covering 33 topics. The exam is time-limited to 20 minutes, so you will not have an opportunity to use a search engine. A passing grade of 70% is required to apply for certification. If you fail the exam, you can pay to take the exam again. You will be unable to apply for certification until you have successfully passed the exam.
Once you’ve paid your exam fee, there is no time limit imposed on when you must take your exam. Feel free to wait as long as you like after paying until you’re ready to take the exam without fear of any penalty. However, once you begin the exam you will only have 20 minutes to answer all 75 questions.
How to Study
Studying for the CEP exam is easy. You can download our Free CEP Study Guide for use, and watch our Ethereum playlist on YouTube as part of your self-study. The 33 topics are covered extensively online, making it easy to learn the knowledge required for certification.
Where to Learn More
C4’s certifications establish a baseline for real-world, practical knowledge in a particular area. Just like a driver’s license proves you understand how to operate a motor vehicle safely, our certifications and standards give you the confidence you need to use cryptocurrencies safely. Learn more about the Certified Ethereum Professional on our website.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.