Table of Contents
Introduction
CCSS covers a list of 10 security aspects of an information system that stores, transacts with, or accepts cryptocurrencies. An information system is a collection of technologies (hardware and/or software), personnel, policies and procedures that work together to provide a secure environment. A security aspect is a discrete technique of securing one piece of an information system. The minimum value of all 10 aspects determines an information system’s overall score within three levels of increasing security: Level I is the lowest and offers strong security measures, while Level III is the highest and offers the most comprehensive security.
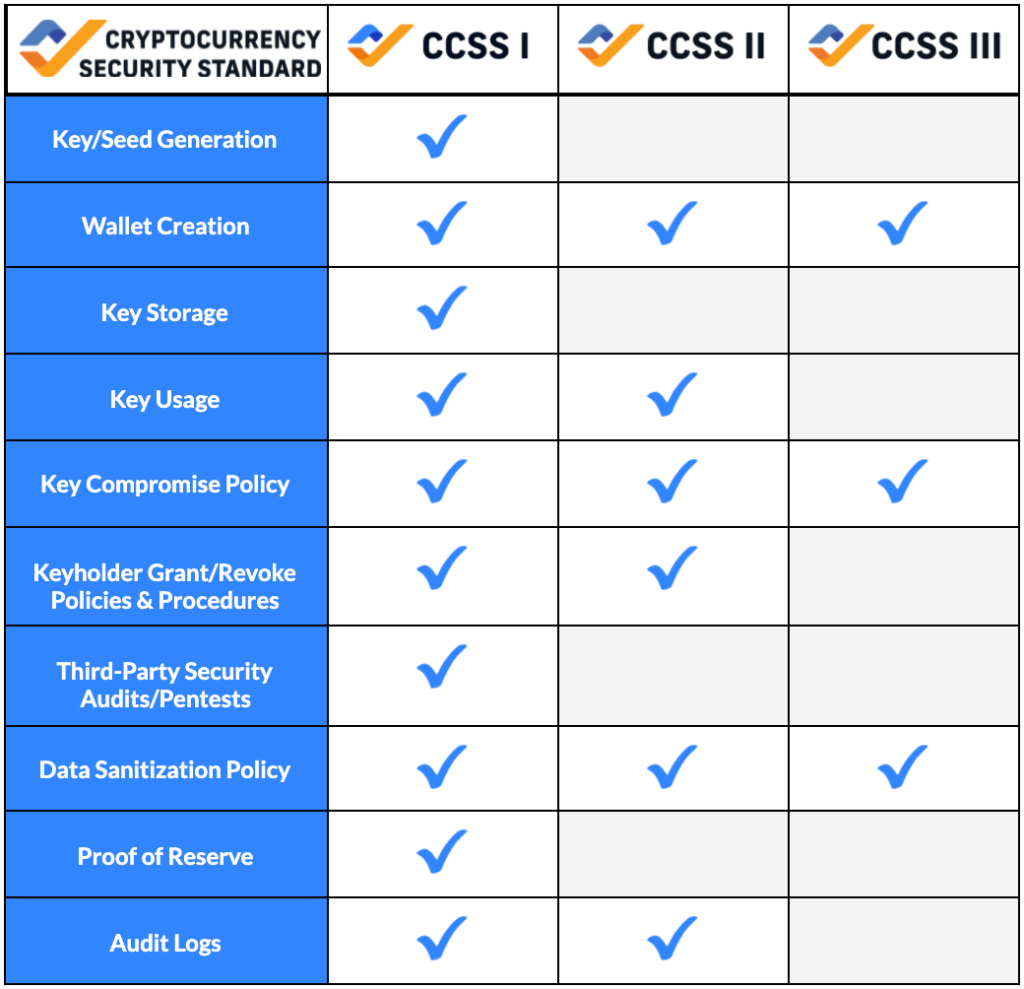
These 10 aspects are organized into 2 domains that help structure the guidelines. These domains are cryptographic asset management and operations. A summary of the standard can be seen in the below example which depicts sample results after auditing Acme Exchange, a “Level I” system. You’ll note that even though there are some aspects with scores in the Level II and Level III range, Acme Exchange is classified a Level I system overall since that is the lowest consistent grade across all aspects:
Acme Exchange’s CCSS Audit Results
Scope
The CCSS covers controls that increase the security of the cryptocurrency portion of an information system, however it does not cover common standards and practices for increasing the cybersecurity of an information system. For this reason, CCSS should be considered as a separate set of recommendations that are applied overtop standard security practices in other domains including business continuity, disaster recovery, network intrusion prevention, physical security, and vulnerability management.
Applicability
The CCSS applies to any information system that makes use of cryptocurrencies. This includes (but is not limited to):
- Cryptocurrency Exchanges (i.e. Information systems that allow its users to exchange cryptocurrencies for other forms of money)
- Cryptocurrency Marketplaces (i.e. Information systems that allow its users to exchange cryptocurrencies for other goods and services)
- Cryptocurrency Games (i.e. Information systems that allow users to gamble their cryptocurrencies for a chance at winning more)
- Cryptocurrency Processors (i.e. Information systems that automate the acceptance of cryptocurrencies for payment)
- Cryptocurrency Storage (i.e. Information systems that facilitate the receipt and transmission of cryptocurrencies amongst other actors)
- Any Information system that handles cryptocurrencies as part of its business logic.
Levels
CCSS is broken into three (3) levels of increasing security. Details of these are outlined in this section.
Level I
An information system that has achieved Level I security has proven by way of audit that they protect their information assets with strong levels of security and most risks to the system’s information assets have been addressed and controls are operating effectively. These controls have been tested by an independent auditor and found to be operating effectively during the audit period.
Level II
An information system that has achieved Level II security has proven by way of audit that they exceed strong levels of security with additional enhanced controls. In addition to covering most risks to the information system’s assets, the use of decentralized security technologies such as multiple signatures have been employed which exceed industry guidelines and provide redundancy if any one key or person becomes unavailable or compromised. These controls have been tested by an independent auditor and found to be operating effectively during the audit period.
Level III
An information system that has achieved Level III security has proven by way of audit that they exceed enhanced levels of security with formalized policies and procedures that are enforced at every step within their business processes. Multiple actors are required for all critical actions, advanced authentication mechanisms ensure authenticity of all data, and assets are distributed geographically and organizationally in such a way to be resilient against compromise of any person or organization. These controls have been tested by an independent auditor and found to be operating effectively during the audit period.
This Repository
This repository is meant to operate as a collaborative document. Your contribution is encouraged.
