
Introduction
The CryptoCurrency Security Standard requires a Data Sanitization Policy as part of the 2.02 Data Sanitization Policy Aspect of CCSS. This aspect involves the elimination of cryptographic keys, seed phrases, and any sensitive information related to key management. Thorough sanitization guarantees the complete destruction of all sensitive information, thereby preventing any potential for data breaches from devices that are no longer in use. These devices include steel plates used for recording seed phrases.
One of the methods for recording seed phrases or passphrases long-term is to punch the 12-24 words from a mnemonic phrase onto steel plates. Steel plates are a popular method because they are not susceptible to electromagnetic attacks, fire (temperature-dependent on metal type), flooding, and are also resistant to other disaster scenarios. Steel plates are more resilient than storing secrets on paper, and less risky, in terms of data degradation and accidental data loss, than storing them on digital media.
However, this begs the questions: How might one go about sanitizing secrets that have been stored on a steel plate? Sanitizing data in accordance with CCSS requirement 2.02.2.1 requires that sanitized media conforms to the National Institute for Standards and Technology (NIST) Special Publications 800-88 recommendation to “clear, purge, or destroy” the media.
As a CCSSA, I have previously completed a CCSS audit and I am part of C4’s CCSS Advocacy Group. As a security advocate, I set out to determine what constitutes ‘cleared’ data for steel plates. Clearing the data is the most realistic method of data sanitization of a metal plate as most will not have access to a furnace that can reach the temperature required to melt metal.
The following walks you, the reader, through this process.
The question I am seeking to answer is:
After you punch your seed phrase or secret onto a steel plate, how effective is it to overwrite that data using this ‘Clear’ method of sanitization? Can the secret be recovered after performing the ‘Clear’ method of overwriting data?
Follow along to see!
The Set-Up
To test the ‘clearing’ of a steel plate, first I purchased a set of steel plates and punches.

To start the experiment I punched the secret ‘PASS123’ into the first cell on the steel plate. This is being used in lieu of a secret seed phrase and will be the data punch and then destroy in each of these attempt. For each type of data destruction I will punch the seed phrase in the same manner and then attempt to destroy the data using different methods.

The Experiment
In this section, I will use a myriad of different “common” hand tools to test their effectiveness and efficiency for sufficiently wiping data punched into steel plates. The purpose of this continued experimentation is to try and find a more time efficient way to destroy the secret punched into the steel plate. I’m going to use the same secret as the above example for each of the tools demonstrated below.
Letter Punch
To keep this simple, I will overwrite the secret with a series of letters and numbers and then check if "three passes," as mentioned in the NIST 800-88 specification, will be sufficient to make the secret unreadable and unrecoverable.
On my first pass to overwrite the data I used the same lettered punches that I used to embed the secret, using an 'X' punch. You can still clearly see the secret.
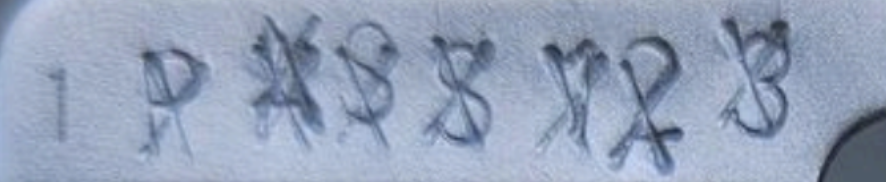
On my second pass to overwrite the data, a 'W' punch was used.
Some of the secret is still visible: The ‘P', the ‘S’s, and ‘2’ and '3’.

On the third pass, I used a number '8' punch.
We can see after the third pass most of the secret is no longer readable, although I can still kind of make out the '2'. If this was a real secret, another pass with another punch would be a good idea to further destroy the original secret and make it unrecoverable.

Using additional punches to overwrite the secret data punched into steel plates until it is no longer readable/recoverable, does seem to be possible to effectively make a secret punched into steel plates unrecoverable using the ‘Clear’ method of data sanitization from the NIST 800-88 standard.
For this method, I would recommend performing at least 3 passes of overwriting the secret data to make it unrecoverable. Perform more passes if the secret is still visible / recoverable.
I would also recommend using punches that cover the top and bottom of the data being overwritten, as to not reveal any information about the individual characters in the secret.
Also, be aggressive with the punches while overwriting data. Give a good punch, not a tap, to better overwrite the data. This applies to any punch method.
There are no additional tools required for overwriting the data in this manner. A potential downside to this approach is that it takes at least 3x longer to sanitize the secret than it took to initially record the secret as the data had to be overwritten 3 times, and to be most effective further overwriting would be advised. It is pretty tedious to overwrite the data character by character as the above example demonstrated.
Summary
Effectiveness: 10 (Highest)
Cost: 3
Effort: 8
Chisel
For this experiment, I used a chisel, which is a wedge shaped metal punch tool, to overwrite the secret. I did not count the number of passes, rather made enough punches for the secret to be overwritten.

This tool is pretty effective at destroying the secret data. I can still make out some of the letters such as ‘A' the ‘2’ and '3’. My chisel was used and the tip was more dull, so a sharp tip (or a new chisel) would likely perform better. The time it took was very short, about a 1 minute or <10 strikes to get the result shown below.

The cost of a set of chisels on Amazon is around $20 and would likely last for as many steel plates as you can destroy. The plate is softer metal so I can't imagine the chisels getting dulled at all from this task.
Summary
Effectiveness: 5
Cost: 3
Effort: 2
Round Tip Punch
I used a round tip punch. Again, I did not count passes, but rather made enough punches for the secret to be overwritten.

Using a round tip punch to overwrite the secret required more work than the chisel but not as much as overwriting it letter by letter. Some of these letters are still visible such as the ‘A' and the 'S’s.
I thought this tool would smush the letters and they would be so mangled they’d be unreadable. I think the effectiveness will depend on how prominent the original secret was punched into the steel.

Summary
Effectiveness: 4
Cost: 4
Effort: 5
Electric Powered Grinder
An electric powered grinder was the ultimate tool to wipe data punched in a steel plate.

The time and effort are the lowest with this tool. As shown in the photo below, I intentionally left some of the letters, but the area that was ground away leaves nothing to recover. Doing this took about 3 seconds, so the time to effectively destroy the secret is minimal.

Summary
Effectiveness: 10
Cost: 5
Effort: 1
Conclusion
In conclusion, the CCSS 2.02 Data Sanitization Policy highlights the critical need for effective methods of data destruction, including when it comes to durable and resilient mediums like steel plates. The exploratory work of CCSSA William Keppler, as detailed in this article, underscores the practical challenges and potential solutions in achieving complete data sanitization.
By experimenting with various tools and methods, from manual punches to electric grinders, Keppler has demonstrated that while traditional overwriting methods can be effective to a certain degree, more aggressive techniques such as grinding offer a far more reliable solution for ensuring that sensitive information is irrecoverable. This aligns closely with the recommendations of NIST SP 800-88, which advocates for a comprehensive approach to clearing, purging, or destroying data. For entities dealing with highly sensitive information, adhering to these stringent standards is a critical component of operational security.
This article was written by Will Keppler, Halborn.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.
