Overview
Cryptocurrencies offer the ability to send secure, irreversible payments to any person anywhere in the world. These borderless technologies are powerful tools for payments — but with this comes power scammers can use to steal, leaving victims with no way to get their money back. There are several common types of crypto scams that any user may encounter. Let’s look at these types of scams and ways to prevent losing money to them.
Types of Scams
Investment Scams
One of the most common scams in the crypto space is the fraudulent “investment” scam. In this type of attack, the thieves trick users into believing they are investing in a lucrative opportunity. In reality, the victim is simply sending cryptocurrency to the scammer’s wallet.
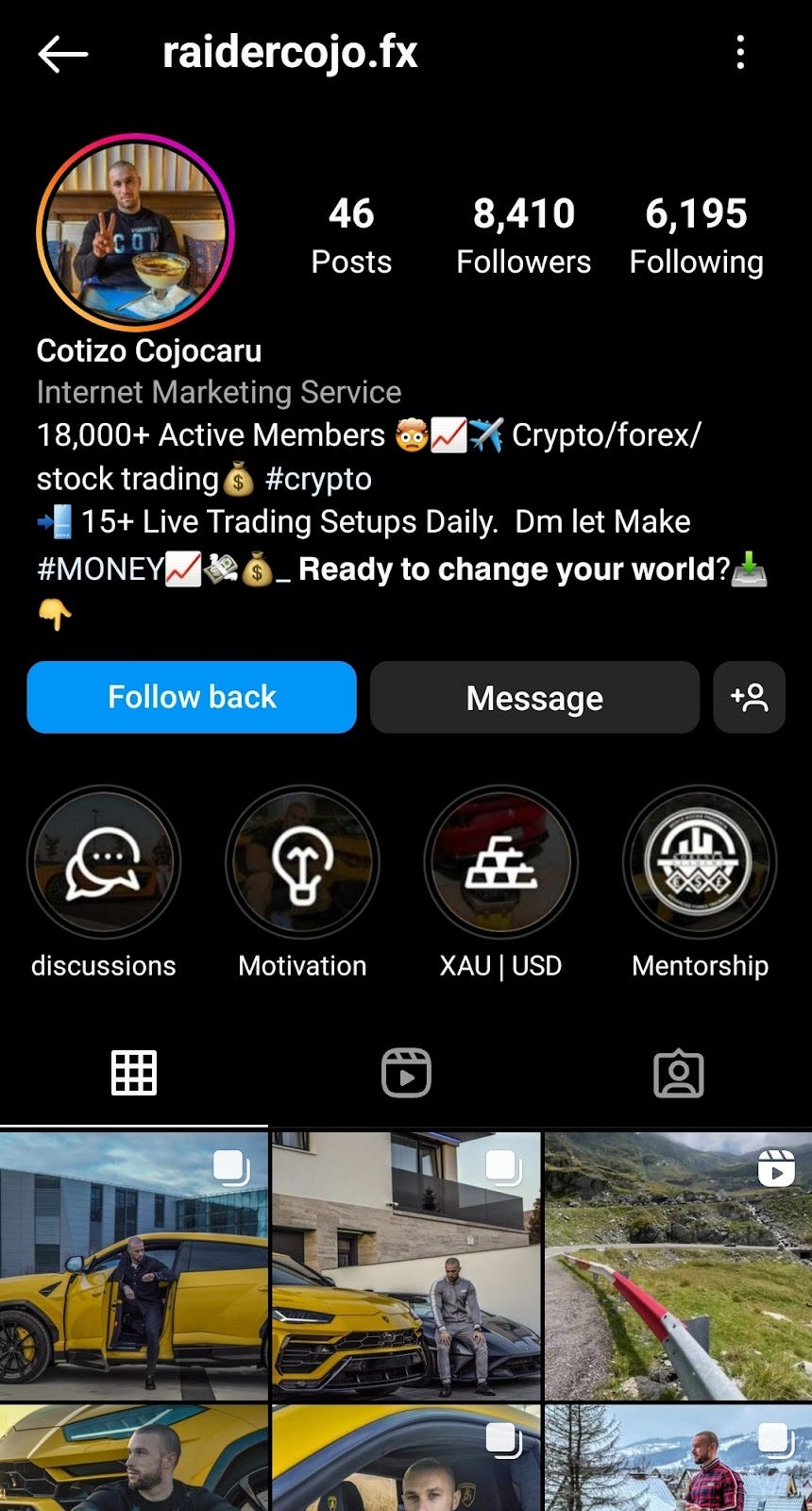
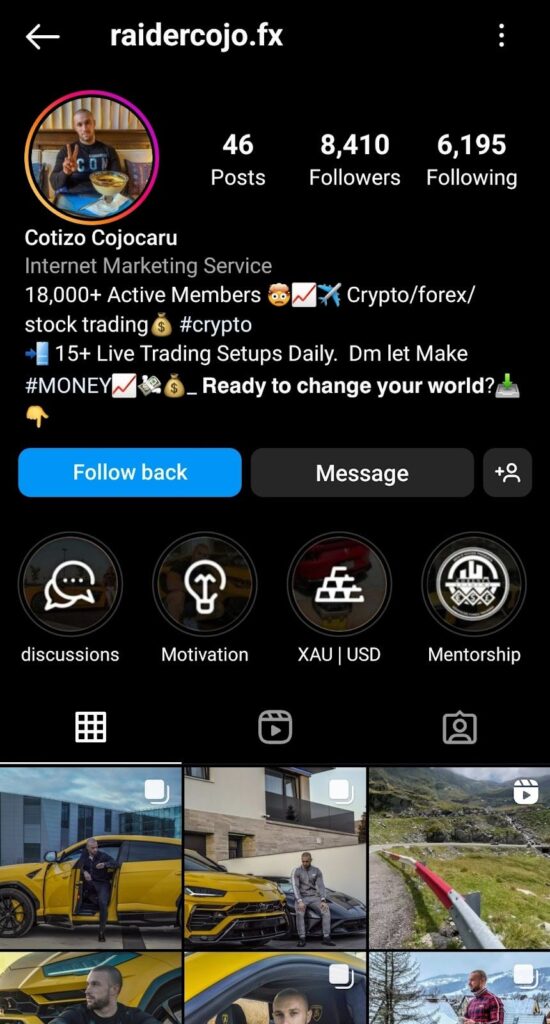
These scams most often start via social media. The perpetrators create convincing profiles of fake “investment managers” that appear to be rich. The name isn’t always a good indicator, but many accounts have “trade” or “fx” (short for foreign exchange) in the name. The accounts have stories or pictures of fake “user withdraws” and fancy cars/houses/lifestyle items to draw you in. The returns promised are too-good-to-be-true, often upwards of 10% per day — this is a red flag.
These scams may also tie-in with impersonation scams, where someone pretends to be a famous person (often related to cryptocurrency) to steal your money. For example, someone pretends to be Andreas Antonopoulos, Roger Ver, or another noteworthy individual.
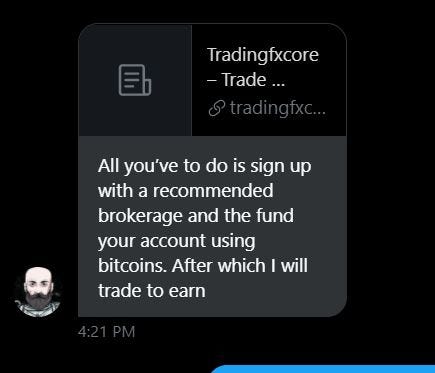
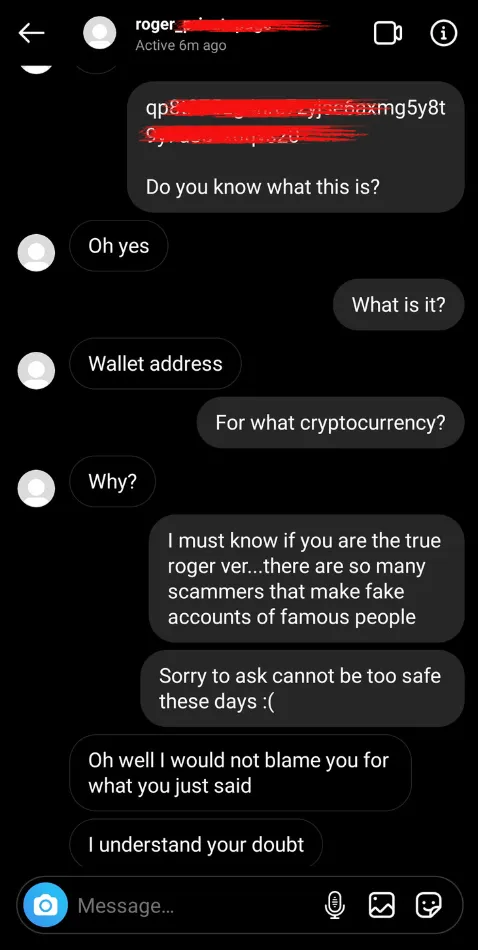


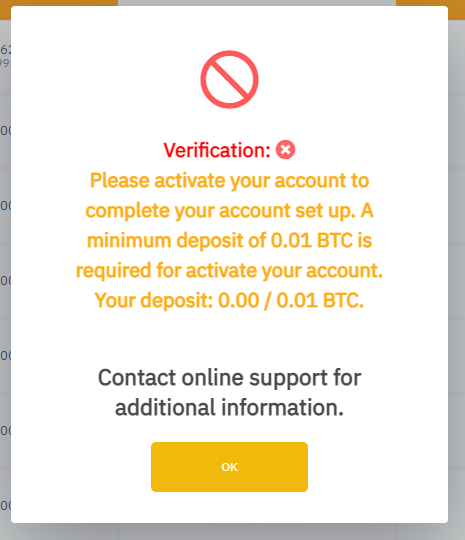
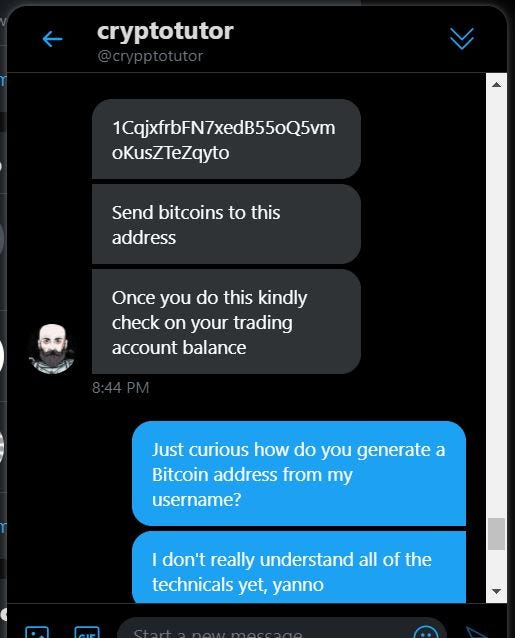
The scammers will initiate a conversation with you unprompted, and lead you to a fake but convincing “trading” website that asks for deposits in cryptocurrency, usually Bitcoin or Ethereum. The website may feature account balances, price information, investment packages, or other information designed to make it appear to be legitimate. They may even have fake but convincing press releases or certifications that make them seem real.
Ultimately, the website and account manager are just a ruse to trick you into thinking you’re involved with a real investment. In reality, you’re simply sending crypto to the scammer’s wallet. These attacks take advantage of crypto’s irreversible nature. Once you send coins to the scammers, you have no ability to get it back. They will often try and convince you into sending more and more money to pay for “taxes” and “withdrawal” fees.
A similar form of the investment scam is the “Cloud Mining” scam. In this variation, scammers ask you to invest money to pay for mining equipment, which the scammers claim will generate returns for you. Just like the typical trading investment scam, cloud mining is all a facade. There is no real mining that happens, and the scammers keep the cryptocurrency you sent to them.
Prevention
You should never send cryptocurrency to anyone pretending to be an investment manager. Only hold cryptocurrency in your own wallets such as a hardware wallet for long term storage. If you wish to store coins with a custodian, stick with well known and vetted exchanges. Understand that cloud mining is not a profitable venture, if not an outright scam. Do a few thorough web searches on any potential platform. Others may have already been scammed and shared a warning on forums, or there may be red flags such as brand-new websites.
Be wary of anyone promising too-good-to-be-true returns, and understand that platforms such as crypto lenders/earning services are substantially more risky than simply holding coins yourself.
Recovery Scams
Sadly, many victims of investment scams fall victim a second time to recovery scams. Once a cryptocurrency transaction is sent and confirmed on the blockchain, there is no way to reverse that payment. Regardless, many victims are desperate to get their money back after losing it to a scam.
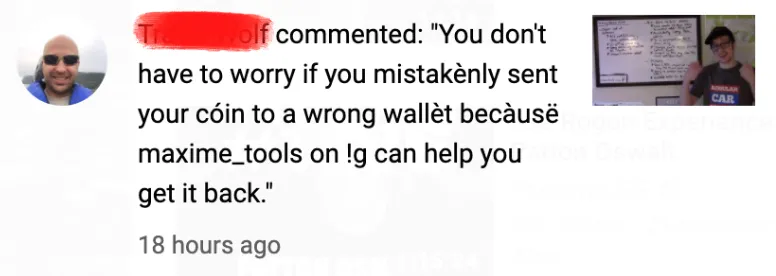
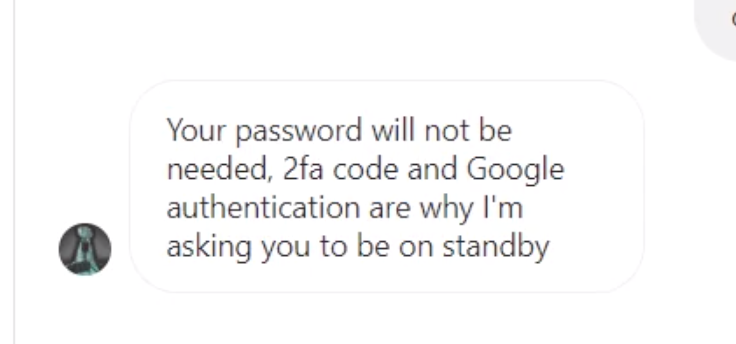
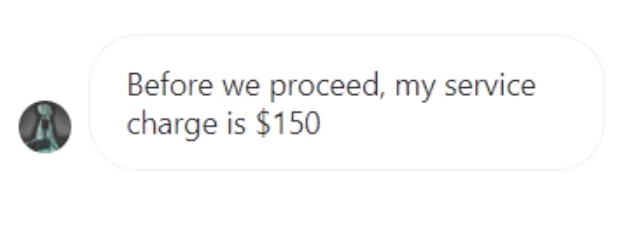
Recovery scammers work by pretending to offer legitimate recovery services, all while tricking users out of more money and accounts. A recovery scammer pretends to have some special technical knowledge or “hack” for retrieving stolen coins, and will offer to do so for a fee. While in the process of your fake “recovery”, the attacker will often steal credentials for exchange accounts or seed phrases so they can clean them out.
These are usually advertised by bots in the comment section of a post or other social media interaction that mentions a scam or technical problem with a wallet. Bots look for certain keywords and then post links or names of the fake recovery scammers.
Prevention
First, understand that cryptocurrency transactions are irreversible. Always double, triple check addresses before sending coins to anyone and be sure the wallet you’re sending to is for a legitimate purpose (such as paying for goods or services). Never send coins to someone claiming they can do the impossible — reverse a transaction. Never give seed phrases, 2FA codes, or passwords to anyone else, even if they claim they are trying to help you.
Phishing Scams
Phishing is one of the most common ways that attackers steal cryptocurrency. In many cases, it is easier to break people than it is to break technology. In other words, tricking you into sending coins, a seed phrase, or another means of stealing your money is easier than hacking a well-designed wallet to steal keys.
These often take the form of seed phrase phishing. A 12–24 word seed phrase grants access to all the coins in a crypto wallet. This is a powerful backup tool, but is also a great target for thieves. Phishing may take the form of an email from a wallet, claiming that you have to “verify” your wallet within 24 hours or your account will be locked. This is a ruse, as you cannot “lock out” a self-custody crypto wallet. This email leads to a form that steals your seed words.
Phishing websites are often sophisticated and very real looking. For example, the real Edge Wallet exists only as a mobile application. And yet, there exist convincing phishing clones like edgewallet.io that steal credentials from the users of the real wallet. These fake platforms can even appear high in search results.
There are also types of computer viruses that replace a copy-pasted address with that of a scammer’s. For example, you copy an address from Coinbase. When you paste it, the software replaces it with the scammer’s. If you don’t double-triple check the address, you inadvertently send it to the thieves.
Prevention
It’s important that you never, ever give your seed phrase to any other person. When entering a backup phrase to restore a wallet, make sure you’re only entering it into the wallet software you intend to use. For example, use a Coinomi seed phrase with a Coinomi or Exodus wallet downloaded from the app store. If it’s a hardware wallet, only enter the seed on the device itself — never into a computer or phone. When sending coins, be sure to double-triple check the address you’ve entered is correct and belongs to the intended recipient. Once coins are sent, there’s no way to reverse the payment.
Giveaway Scams
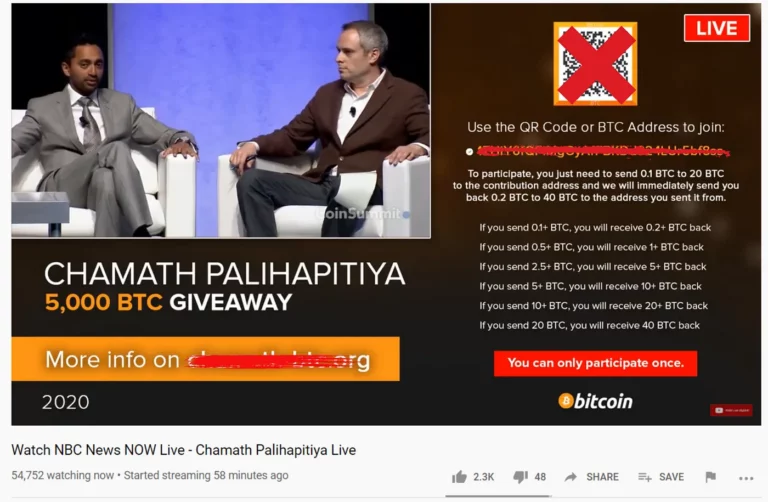
Who doesn’t love free money? Most of us do! The final type of scam in this article will discuss the giveaway scam. Giveaway or “Doubling” scams trick a user into sending coins to a scammer’s address with the promise of an airdrop or free cryptocurrency in return.
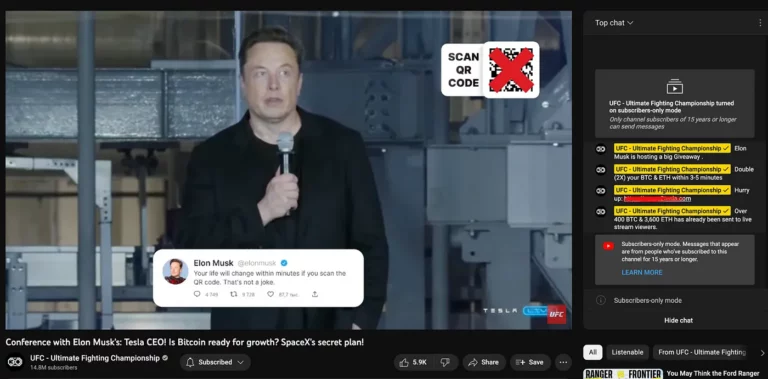
These usually use the image of rich and famous people or organizations to lend legitimacy to the scam. Sometimes the legitimate accounts of these people are hacked/stolen to promote scams. In one example, the MMA organization the UFC had their YouTube account compromised and used to promote a scam.
Fake airdrop scams operate similarly to investment scams with a slightly different angle. Instead of asking you for cryptocurrency to “verify” your address, these fake airdrop platforms promise free tokens by connecting your wallet to the website. For example, by using WalletConnect, a seed phrase, or a browser wallet extension such as MetaMask. The website then uses those permissions to steal all of your coins and tokens. Remember, there is no such thing as free money!
Prevention
Never send cryptocurrency to anyone with the promise of a return. Cryptocurrency transactions are irreversible, so if you send coins to a scammer there is no way to get them back. Never connect to a website using WalletConnect or MetaMask with the promise of an airdrop, as this can be used to steal your funds. As well, cryptocurrencies use public key cryptography. Your address is safe to share, and nobody can use only your address to steal coins. If someone truly wants to give you crypto for free, you only have to give them your public address.
Avoiding Scams
In general, most scams start with a too-good-to-be-true promise. Either a lucrative investment opportunity, or a chance at a giveaway, or even the possibility of returning lost coins. Always ask yourself if something sounds too good to be true before getting involved. As well, always understand that cryptocurrency transactions are irreversible — once coins are sent there is no way to get them back. Take your time before sending, before entering a seed phrase anywhere but a wallet, or interacting with others on social media.
This article was written by our CryptoCurrency Essentials (CCE) Committee, with special thanks to committee member Josh McIntyre.
Disclaimer
The information presented in this article is for educational and informational purposes only. It does not constitute financial advice, investment recommendations, or any form of endorsement.
The views and opinions expressed by individuals in this article are solely those of the speakers and do not necessarily represent those of C4 or any other organizations with which they are affiliated.
The mention or inclusion of any individuals, companies, or specific cryptocurrency projects in this video should not be considered as an endorsement or promotion.
Regulations and legal frameworks around cryptocurrencies may vary in different jurisdictions. It is your responsibility to comply with the applicable laws and regulations of your country or region.